Introduction
Trusted Computing (TC) has been a popular research field of information security in recent years. In this report, we collect, categorize, and briefly summarize 19 TC-related papers from ACM CCS, NDSS, IEEE S&P, and USENIX Security conferences in 2023 and 2024, to identify common patterns and trends in this field.
The papers are categorized into six topics: vulnerability discovery, novel attack, novel defense, performance enhancement, TEE extension, and TEE application, as shown in the following table. These topics provide a systemic view of TC security.
| Topic | Research |
|---|---|
| Vulnerability Discovery | EnclaveFuzz [1], SyzTrust [10], TEEzz [15], Pandora [7], SymGX [12] |
| Novel Attack | BusFaultAttack [5], UnTrustZone [9], SGXRacer [17] |
| Novel Defense | TEE-SHirT [3], Sense [4], TEESlice [8], MyTEE [13], Capstone [16] |
| Performance Enhancement | RR [14], ReusableEnclaves [18] |
| TEE Extension | LDR [2], Shelter [19], Acai [11] |
| TEE Application | TrustSketch [6] |
The collection (19 papers on various topics in only two years) implies that TC is a promising direction in academic research.
We will review the six aforementioned topics to learn more about this field. Notably, topics with more than one line in the table above are divided into sub-topics per line.
Topic 1: Vulnerability Discovery
Two typical approaches are investigated for TC vulnerability discovery: fuzzing and symbolic execution.
Sub-topic 1: Fuzzing
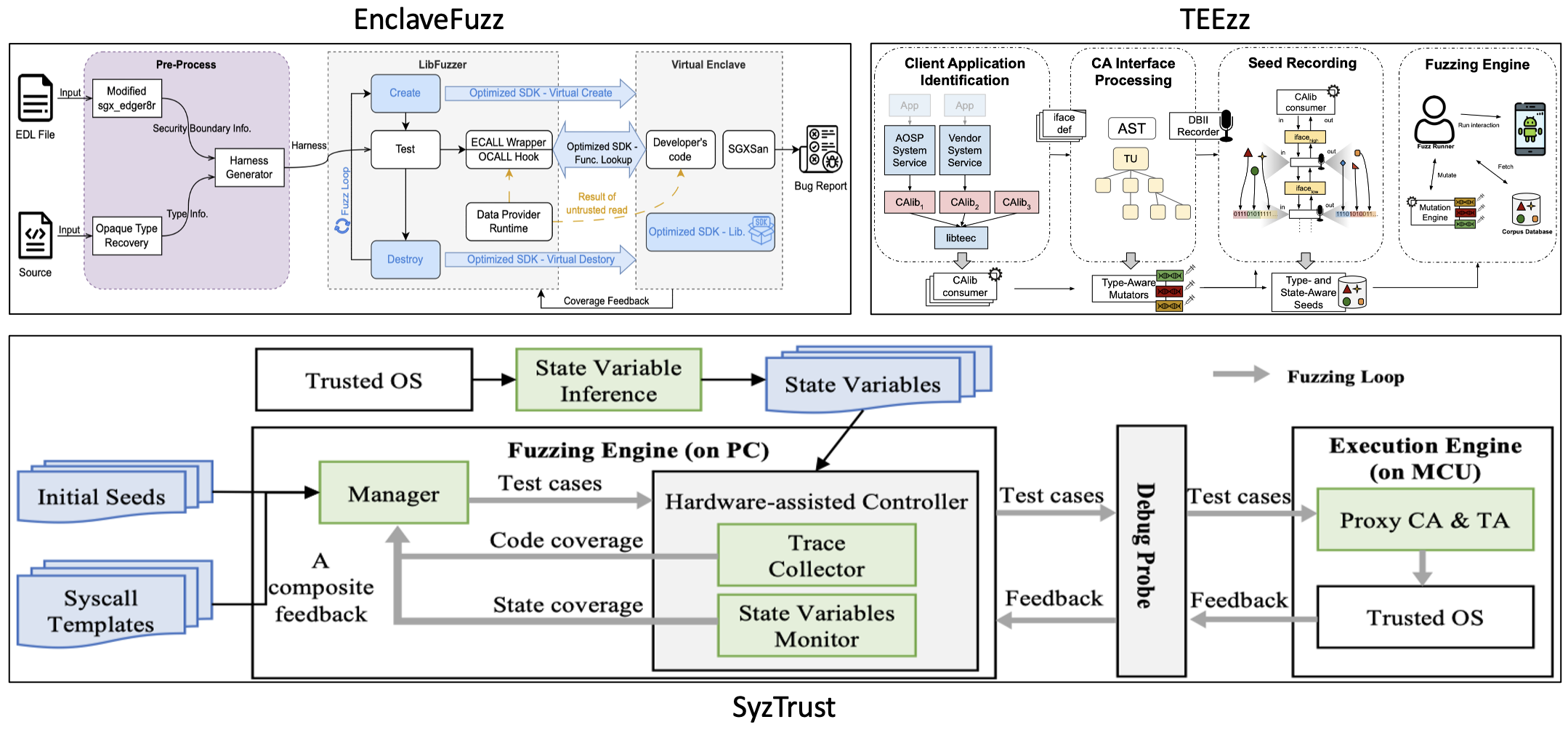
EnclaveFuzz [1] is a multi-dimension structure-aware fuzzing framework for Intel SGX applications, which analyzes enclave sources to extract input structures and correlations, then generates fuzz harnesses that can produce valid inputs to pass sanity checks.
TEEzz [15] is a TEE-aware fuzzing framework for Arm TrustZone based trusted applications (TA) on commercial-off-the-shelf (COTS) Android devices, which tries to automatically infer the field types and message dependencies of the TA API through its interactions, designing state- and typeaware fuzzing mutators, and creating an in situ, on-device fuzzer.
SyzTrust [10] is a state-aware fuzzing framework for resource-limited Trusted OSes, which fuzzes Trusted OSes directly on IoT devices as well as tracking state and code coverage non-invasively. SyzTrust utilizes composite feedback to guide the fuzzer to effectively explore more states as well as to increase the code coverage.
Sub-topic 2: Symbolic Execution
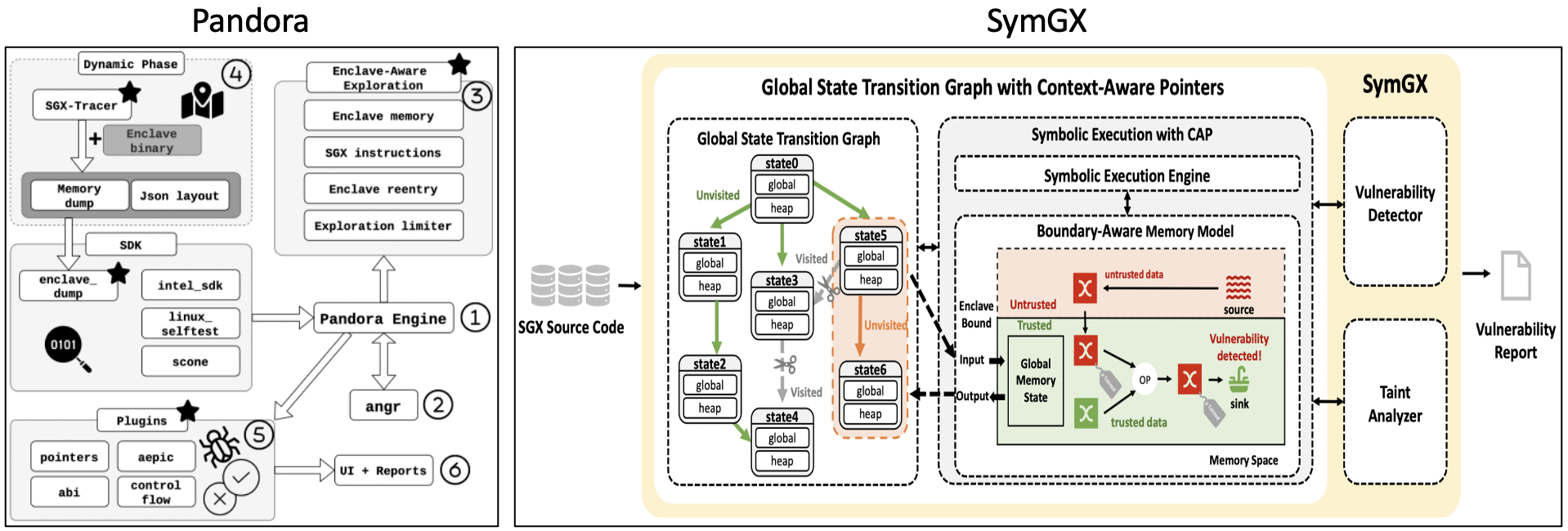
Pandora [7] is an enclave-aware symbolic execution tool, providing runtime-agnostic validation for numerous Intel SGX Enclave runtimes.
SymGX [12] is a symbolic execution-based vulnerability detector for detecting cross-boundary pointer vulnerabilities, which leverages a new analysis model, Global State Transition Graph with Context Aware Pointers (GSTG-CAP), that simulates properties-preserving execution behaviors for Intel SGX applications.
Topic 2: Novel Attack
Two types of TC attacks are studied in the related papers: hardware attacks and software attacks.
Sub-topic 1: Hardware Attacks
BusFaultAttack [5] present malicious Trusted Application loading and symmetric encryption keys stealing in Arm TrustZone, by injecting electromagnetic pulses onto the system bus during the execution of instructions involving processor-memory interaction.
UnTrustZone [9] uncovers a new threat to all forms of on-chip crypto: long-term data remanence, which allows attackers to imprint and exfiltrate secrets from a range of SRAM-based memories.
Sub-topic 2: Software Attacks

SGXRacer [17] is proposed as a lockset-based binary analysis detection for controlled data race attacks (where the adversary controls the underlying operating system and manipulates the scheduling of enclave threads and handling of interrupts and exceptions) in Intel SGX SDKs and projects.
Topic 3: Novel Defense
The defense mechanisms proposed in related papers are coarsely categorized into three types: mechanisms against side-channel attacks, mechanisms against privacy-stealing attacks and other designs.
Sub-topic 1: Against Side-channel Attacks (SCA)
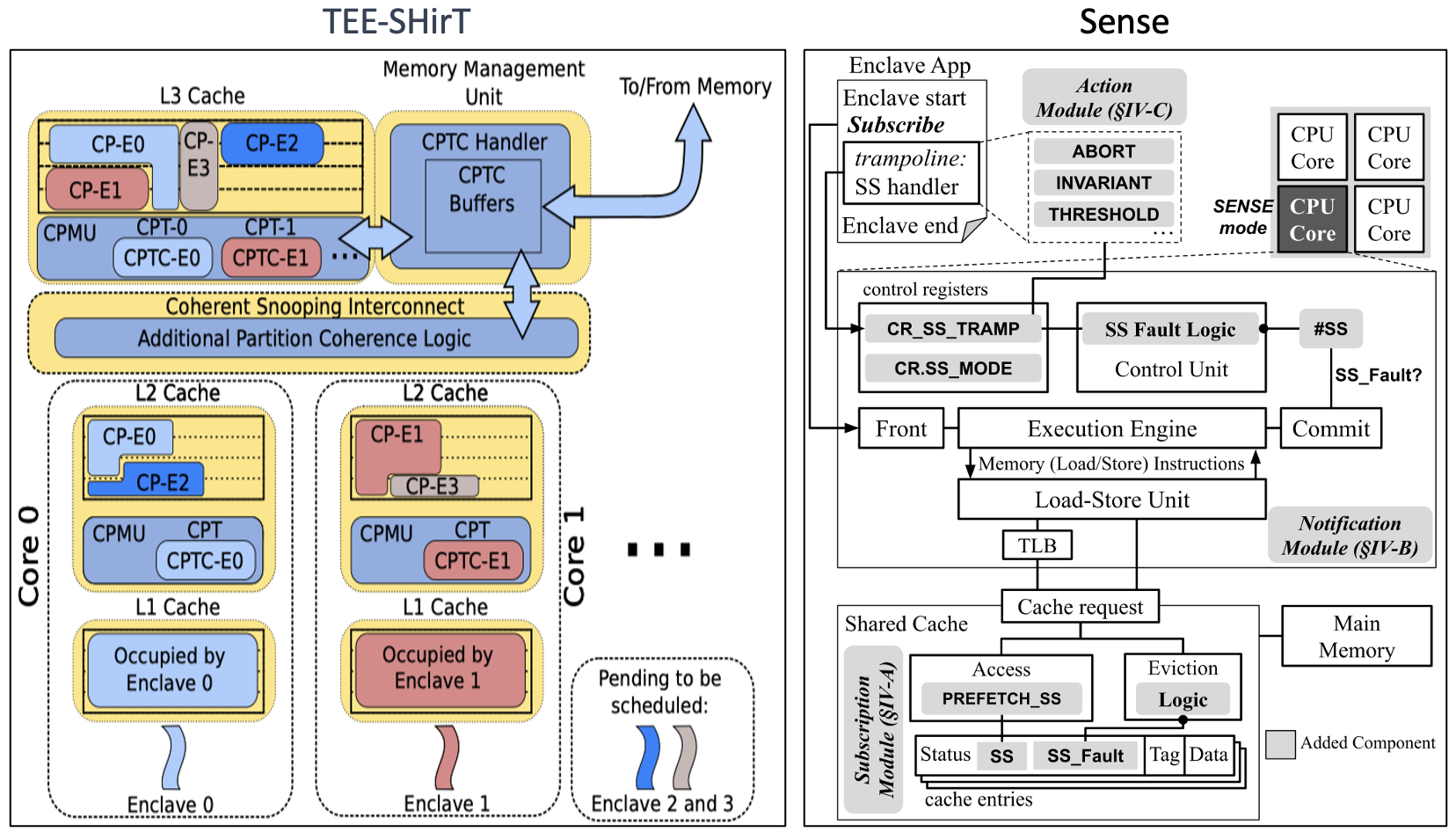
TEE-SHirT [3] is a framework for efficient and secure fine-grained partitioning of cache hierarchies, which consists of partitioned shared last-level cache, partitioned private L2 caches, and nonpartitioned L1 caches that are flushed on context switches and system calls.
Sense [4] is a solution that actively exposes underlying microarchitectural information to userspace TEEs, enabling userspace software in TEEs to subscribe to fine-grained microarchitectural events and utilize the events as a means to contextualize the ongoing microarchitectural states.
Sub-topic 2: Against Privacy-stealing Attacks
TEESlice [8] is a novel TEE-Shielded DNN Partition (TSDP) method that defends against model stealing (MS) and membership inference attack (MIA) during DNN inference.
Sub-topic 3: Other Defense Designs
MyTEE [13] is a solution that enables a TEE to be built even in worstcase environments wherein major hardware security primitives (e.g., ARM TrustZone extensions for memory access control) are absent, which crafts page tables for memory isolation, filters DMA packets, and enables secure IO.
Capstone [16] is a more expressive architectural capability design that supports multiple existing memory isolation models in a trustless setup, i.e., without relying on trusted software components.
Topic 4: Performance Enhancement
RR [14] is a fault model for replicating TEEs, which precisely captures the possible fault behaviors of TEEs with external state.
ReusableEnclaves [18] enables rapid enclave reset and robust security with three key enabling techniques: enclave snapshot and rewinding, nested attestation, and multi-layer intra-enclave compartmentalisation, which reduces the cold start overhead in an end-to-end serverless setting while imposing a reasonable performance impact on standard execution.
Topic 5: TEE Extension
LDR [2] is a TEE driver execution environment, which reuses functions in both the TEE OS and normal world Linux kernel to run a TEE device driver and address related security issues.
Shelter [19] is a complement to Confidential Compute Architecture (CCA)’s primary Realm VM-style architecture, based on Arm CCA hardware primitive available in Armv9.2, which allows third-party developers to deploy their applications with isolation in userspace.
Acai [11] extends ARM CCA security invariants to device-side (e.g., GPUs and FPGAs) access to address several critical security gaps.
Topic 6: TEE Utilization
TrustSketch [6] is a general framework for trustworthy sketch telemetry based on Intel SGX, supporting lots of sketching algorithms, able to detect a wide range of attacks on sketch-based telemetry in a timely fashion while incurring only minimal overhead.
References
NDSS'24
- Chen, Liheng, et al. “EnclaveFuzz: Finding Vulnerabilities in SGX Applications.”
- Yan, Huaiyu, et al. “LDR: Secure and Efficient Linux Driver Runtime for Embedded TEE Systems.”
- Arıkan, Kerem, et al. “TEE-SHirT: Scalable Leakage-Free Cache Hierarchies for TEEs.”
- Sang, Fan, et al. “SENSE: Enhancing Microarchitectural Awareness for TEEs via Subscription-Based Notification.”
- Nimish, Mishra, et al. “Faults in Our Bus: Novel Bus Fault Attack to Break ARM TrustZone.”
- Cheng, Zhuo, et al. “TRUSTSKETCH: Trustworthy Sketch-based Telemetry on Cloud Hosts.”
SP'24
- Alder, Fritz, et al. “Pandora: Principled Symbolic Validation of Intel SGX Enclave Runtimes.”
- Zhang, Ziqi, et al. “No Privacy Left Outside: On the (In-) Security of TEE-Shielded DNN Partition for On-Device ML.”
- Mahmod, Jubayer, and Matthew Hicks. “UnTrustZone: Systematic Accelerated Aging to Expose On-chip Secrets.”
- Wang, Qinying, et al. “SyzTrust: State-aware Fuzzing on Trusted OS Designed for IoT Devices.”
Security'24
- ShwetaShinde, S. S. A. B. B. S. M. K. “ACAI: Protecting Accelerator Execution with Arm Confidential Computing Architecture.”
CCS'23
- Wang, Yuanpeng, et al. “SymGX: Detecting Cross-boundary Pointer Vulnerabilities of SGX Applications via Static Symbolic Execution.”
NDSS'23
- Han, Seung-Kyun, and Jinsoo Jang. “MyTEE: Own the Trusted Execution Environment on Embedded Devices.”
- Dinis, Baltasar, Peter Druschel, and Rodrigo Rodrigues. “RR: A Fault Model for Efficient TEE Replication.”
SP'23
- Busch, Marcel, et al. “Teezz: Fuzzing Trusted Applications on COTS Android Devices.”
Security'23
- Yu, Jason Zhijingcheng, et al. “CAPSTONE: A Capability-based Foundation for Trustless Secure Memory Access.”
- Chen, Sanchuan, Zhiqiang Lin, and Yinqian Zhang. “Controlled Data Races in Enclaves: Attacks and Detection.”
- Zhao, Shixuan, et al. “Reusable Enclaves for Confidential Serverless Computing.”
- Zhang, Yiming, et al. “SHELTER: Extending Arm CCA with Isolation in User Space.”